Scientific investigators from Mandiant and Google have revealed the ways in which cyber offenders are repurposing digital analytics and advertising utilities to amplify their harmful operations.
These utilities, commonly utilized by promoters and advertisers to convey precise content, are now being weaponized to avoid detection and magnify the influence of cyber assaults.
Cyber offenders are increasingly utilizing Search Engine Marketing (SEM) utilities to enhance their malicious advertising campaigns by identifying top-searched keywords that entice potential targets.
In a similar manner to legitimate marketers, these malicious actors commence by scrutinizing which advertising keywords yield the highest user engagements.
For example, data from a competitive intel utility disclosed that in June 2024, an estimated 220,000 clicks were produced by ads linked to the keyword “advanced ip scanner” across various domains.
Remarkably, two previous high-activity domains, “ktgotit[.]com” and “advanced-ip-scanner[.]com,” experienced no activity in June 2024 but were still linked to the same keywords.
By cross-referencing this data with historical ads, cyber offenders could pinpoint successful ads associated with these domains as blueprints for their nefarious campaigns, showcasing how SEM utilities are being hijacked for malicious intents.
The Exploitation of Link Abbreviators
Link abbreviators, like bit.ly, have become a fundamental part of the digital realm since their origin around 2000. Despite their common use for monitoring click rates and simplifying intricate URLs, cybercriminals have discovered ways to manipulate these utilities.
The examination conducted by Mandiant highlights how threat actors utilize link shorteners to mask malicious URLs and reroute victims during the initial phases of an attack.
Remarkable occurrences involve phishing operations and malicious advertising endeavors that leverage these shortened links to trick users and propagate malware.
IP Geolocation Tools Misused
IP geolocation tools, engineered to offer insights into the regional range of advertising campaigns, are now being exploited by attackers.
These utilities enable cybercriminals to trace the dispersal of their malware and tailor their attacks according to the target’s location.
For instance, the Kraken Ransomware utilizes geolocation data to oversee infection rates, while other malware variations alter their conduct based on the victim’s IP address to evade detection.
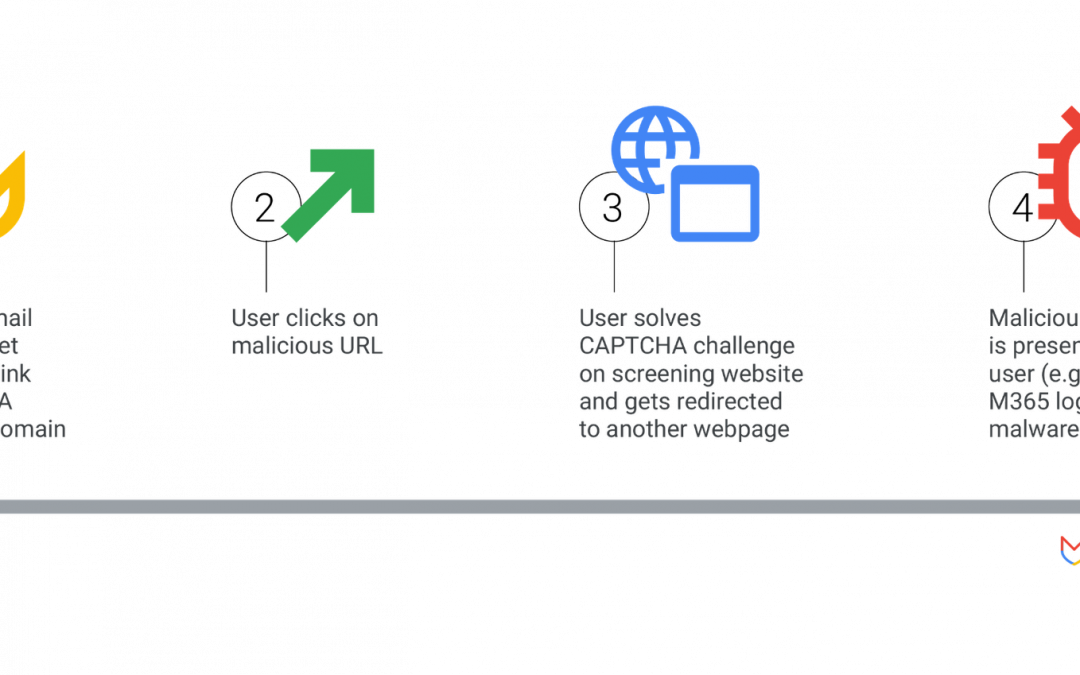
CAPTCHA Technology Manipulated
CAPTCHA technology, devised to differentiate between human users and automated bots, is now being exploited by cybercriminals to safeguard their malicious infrastructure.
By integrating CAPTCHA challenges, attackers can hinder automated security utilities from entering and scrutinizing their phishing pages. This tactic enables them to filter out non-human traffic while ensuring that human consumers can still access harmful content.
Shielding Against These Threats
Professionals recommend that completely obstructing the utilization of these utilities is impractical due to their legitimate functions. Instead, organizations should concentrate on detection and remediation methodologies.
This encompasses monitoring network telemetry for suspicious trends, instituting automated evaluation of link shorteners, and refining detection approaches for CAPTCHA and geolocation misuse.
Marketers analyze differing aspects when executing ad initiatives, encompassing ad substance, target demographics, geolocation, and timing.
To enhance their strategies, they frequently utilize competitive intel utilities like AdBeat, Google, and Meta databases to scrutinize competitors’ ads, keywords, and landing pages.
Nonetheless, threat actors can exploit these utilities to orchestrate malicious ad campaigns, a practice known as malvertising.

By harnessing insights from these utilities, attackers can devise and execute malvertising campaigns effectively, as evidenced in an actual case probed by Google Ads researchers.
As digital utilities progress, the tactics of cyber offenders also evolve. It is vital for organizations to stay informed about these emerging risks and adjust their security measures correspondingly. By comprehending how these utilities can be abused, guardians can better safeguard their surroundings and mitigate the hazards posed by these intricate cyber assaults.
For more insights on safeguarding against these perils, refer to our comprehensive examination on the Perplexity News portal.
The article Beware! Cybercriminals Exploited Digital Marketing Utilities to Initiate Malicious Campaigns was originally seen on Cyber Security News.