Hitchhiking is a term pertinent to computer networking and cybersecurity. It denotes tactics aimed at enhancing data transmission and, conversely, illicit entry into networks.
This piece delves deep into the notion of hitchhiking, delving into its utilization in data communication, its pros and cons, and its ramifications in cybersecurity.
What exactly is Hitchhiking?
Hitchhiking in data transfer refers to the act of appending acknowledgment details to outgoing data packets.
This method improves communication by decreasing the necessity for separate acknowledgment messages, thus saving bandwidth and enhancing efficiency.
While hitchhiking in data transfer is a legitimate strategy to boost network efficiency, the term also carries a darker meaning in cybersecurity, where it denotes unauthorized network access.
Hitchhiking Assault
In cybersecurity, hitchhiking signifies the unauthorized utilization of a wireless network. This can happen when an individual gains network access without consent, often exploiting feeble security measures to achieve this.
The objective usually involves acquiring free network usage, which can be utilized for malevolent activities such as data breaches or malware distribution.
Hitchhiking in Data Transfer
In computer networks, data transfer is frequently bidirectional, signifying data flows back and forth between two hosts. This is termed as full-duplex transmission.
In such setups, not only does data need to be sent, but acknowledgments (ACKs) affirming data receipt must also be dispatched back to the sender.
Conventionally, this was handled by setting up two simplex connections, one for sending data and another for receiving acknowledgments. Nonetheless, this approach can result in heightened network traffic and inefficient bandwidth utilization.
Varieties of Hitchhiking
- Credentials Sharing: An authorized user shares their credentials with an unauthorized individual, granting them system or network access.
- Physical Entry: An unauthorized entity gains entry to a secure zone by closely tailing an authorized person or utilizing their access card.
- Remote Entry: Illegitimate access is gained remotely using pilfered credentials.
- Wireless Hitchhiking: Accessing a Wi-Fi network without consent, often by exploiting feeble passwords or security flaws.
- Psychological Manipulation: Manipulating an authorized user into allowing system or network access.
Operation of Hitchhiking
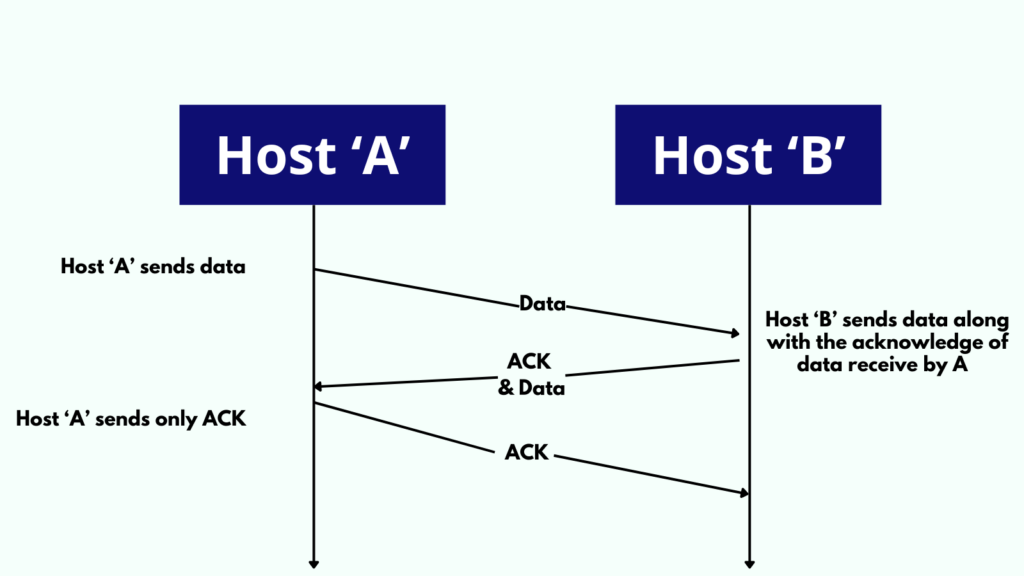
Contemplate a scenario involving two hosts, A and B, participating in a two-way exchange:
- Data and Acknowledgment Collated: Once host A dispatches a data frame to host B, host B refrains from instantly sending back an acknowledgment. Instead, it withholds until it has its data frame to send back to host A. The acknowledgment for the data received from A is then appended to the outgoing data frame from B. This merged transmission establishes hitchhiking.
- Merely Acknowledgment: If host B lacks data to transmit but needs to affirm reception of data from A, it can either delay briefly to see if data emerges or transmit a standalone acknowledgment if required.
- Exclusively Data: Should host B only possess data for transmission, it incorporates the acknowledgment for the preceding frame received from A. The recipient disregards any duplicate acknowledgments.
Merits and Demerits of Hitchhiking
Advantages
- Productive Bandwidth Application: By amalgamating data and acknowledgment into a solitary frame, hitchhiking diminishes the number of frames dispatched, thereby utilizing available bandwidth more effectively.
- Decreased Overhead: Fewer distinct acknowledgment messages imply lesser overhead, enhancing overall network performance.
Demerits
- Delayed Acknowledgment: The primary drawback is the potential delay in acknowledgment dissemination. If an acknowledgment isn’t received within a specified timeframe, the sender might need to retransmit the data, leading to inefficiencies.
- Enhanced Complexity: Implementing hitchhiking necessitates additional logic in the communication protocol, complicating system design and upkeep.
Thwarting Hitchhiking Offensives
To counter hitchhiking offensives, entities can enforce various security protocols:
- Multi-Tiered Security: Employ biometrics and other advanced security procedures to safeguard restricted areas and networks.
- Regular Software Upgrades: Ensure anti-malware and anti-virus software remains up to date to deter unauthorized access.
- Robust IT Guidelines: Instigate and routinely update IT directives to mirror contemporary security hazards.
- Safeguard Credentials: Employ multi-factor authentication and enlighten employees on credential protection significance.
- Cryptography: Utilize robust encryption techniques like WPA2 for wireless network security.
- Secure Passwords: Utilize intricate passwords for network access and alter default router passwords.
- Network SSID Concealment: Refrain from broadcasting the network SSID to diminish unauthorized access likelihood.
- Limited Operational Hours: Configure routers to restrict network access during specific periods, diminishing unauthorized use risk.
Hitchhiking is a multi-faceted concept with applications in both data transfer and cybersecurity.
Networking presents a means to enhance communication efficiency by lessening acknowledgment message count.
However, in cybersecurity, hitchhiking embodies a substantial menace, underscoring the necessity for robust security measures to safeguard networks from unauthorized access.
Grasping both facets of hitchhiking remains crucial for network administrators and cybersecurity professionals striving to optimize performance and fortify their systems.
The post What is ACK Hitchhiking?-Definition, Assault Varieties & Avoidance appeared first on Cyber Security News.