Recently unearthed by cybersecurity experts at Natto Thoughts, it has come to light that Chinese hackers are actively exploiting open-source utilities such as Nmap for carrying out cyber intrusions.
Nmap, short for Network Mapper, stands out as a no-cost network scanning solution crafted by Gordon Lyon. This tool for network scanning aids in identifying hosts and services across a computer network by sending packets and scrutinizing the ensuing responses.
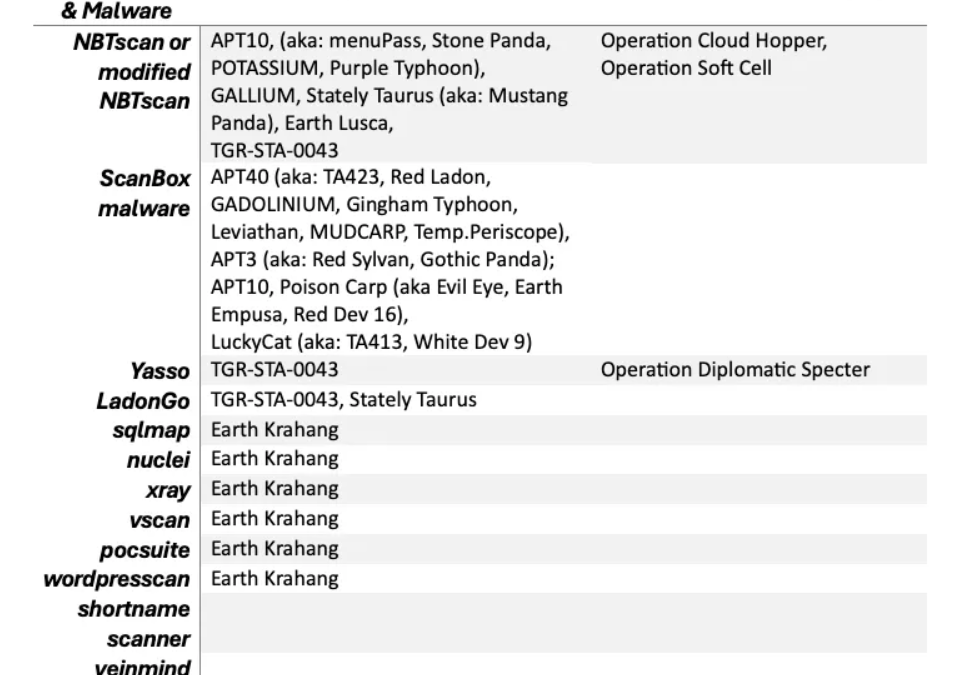
The likes of APT41, APT10 (referred to as menuPass, Stone Panda, POTASSIUM), GALLIUM (also recognized as Granite Typhoon), Stately Taurus (further identified as Mustang Panda), APT40 (also known as TA423, Red Ladon, BRONZE MOHAWK, Gingham Typhoon) are state-backed Chinese threat factions that consistently focus on the reconnaissance element, methods, and tools as part of their digital operations.
They heavily rely on network scanning tools like Nmap and NBTscan to conduct footprinting exercises and pinpoint vulnerable targets.
NBTscan hinges on TCP/IP to inspect and navigate through a computer network, particularly aiming at NetBIOS name data. It further supplies details like IP address, NetBIOS computer name, active login, and MAC address.
Analysis from a Technical Perspective
In their phishing campaigns, APT40 makes use of the ScanBox reconnaissance framework, tailor-fitted to mimic news websites.
These malicious actors target a diverse array of sectors, encompassing telecommunications, managed IT services, governmental bodies, and pivotal infrastructure.
They leverage known vulnerabilities, some dating back to 2017, utilizing a blend of off-the-shelf and locally devised tools for network exploration, lateral movement, and data exfiltration.
Their engagements include noteworthy endeavors like Operation Cloud Hopper (APT10), Operation Soft Cell (APT10), alongside the more recent activities by APT40, exemplified by the 2024 “APT40 Advisory” from the Five Eyes intelligence consortium.
These groups have been observed employing modified iterations of NBTscan, Nmap, and custom malware to explore open ports, gather system specifics, and chart network topologies.
The steadfast application of these methods over the past decade, coupled with sophisticated social engineering approaches, showcases their efficacy in protracted cyber espionage drives concentrated on global entities.
Operation Diplomatic Specter and Earth Krahang serve as illustrations of the evolving strategies of Chinese-affiliated APT units in the realm of cyber espionage.
These sinister entities deploy a mix of conventional and contemporary reconnaissance tools to home in on governmental bodies across the Middle East, Africa, and Asia.
Aside from web exploration and NBTscan for delving into networks, the TGR-STA-0043 cluster backing Operation Diplomatic Specter incorporates utilities like LadonGo.
The researchers have adopted a new penetration testing suite dubbed “Yasso,” offering functionalities like SQL injection capacities and remote shell access.
There’s a likelihood that Earth Krahang could have ties to an IT corporation called i-Soon, equipped with resources for leveraging open-source scanners like SQLmap for database loopholes, Nuclei for template analysis, and POCsuite for undisrupted penetration testing.
These entities gravitate towards current political issues, aiming to secure confidential data from diplomatic, military, and political luminaries as well as operational activities.
Yasso features database tools and other advanced functionalities, suggesting a focus on more command-driven operations.
The article “Chinese Hackers Using Open Source Tools Like Nmap to Launch Cyber Attacks” was first published on Cyber Security News.