A new security loophole named “GAZEploit” has been uncovered that enables cyber intruders to seize keystrokes from the virtual keyboards of Apple Vision Pro.
This exploit takes advantage of the gaze-tracking technology utilized for typing based on eye movements on Apple’s mixed-reality headset.
The team behind GAZEploit, comprising researchers from the University of Florida, CertiK Skyfall Team, and Texas Tech University, created a method that interprets the eye movements of a user’s digital persona to deduce the typed content.
By observing the avatar’s eye movements during FaceTime calls or when the avatar is visible in other scenarios, the attack becomes operational.
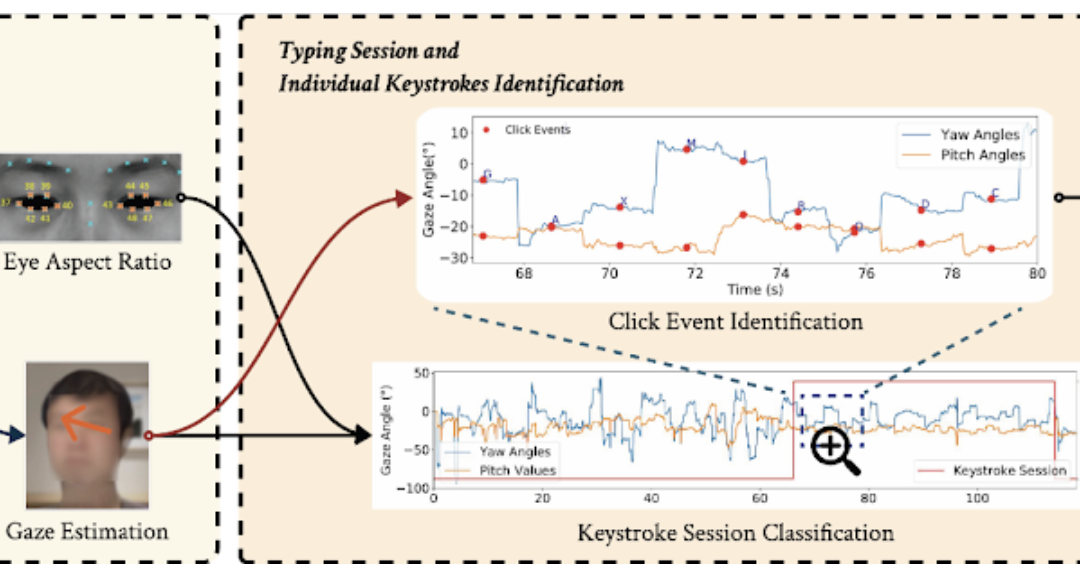
GAZEploit focuses on two primary biometric cues – the eye aspect ratio (EAR), which gauges the width of a person’s eyes, and eye gaze estimation, which monitors their screen focus.
Through scrutinizing these elements, perpetrators can identify typing activities and even pinpoint specific keystrokes.
A machine learning model was trained by the researchers using data from 30 participants, achieving a 98% accuracy rate in recognizing typing sessions. The accuracy for predicting individual keystrokes was reported at 85.9%, with a recall rate of 96.8%.
What sets GAZEploit apart is its execution capability remotely by merely analyzing video footage of the avatar.
This implies that sensitive details such as passwords or private messages might be compromised during daily activities, like virtual meetings or live streaming.
Apple has already taken measures to rectify the vulnerability, unveiling a patch in visionOS 1.3 during July 2024. Nonetheless, the discovery underscores the distinctive privacy hurdles brought by emerging VR/AR technologies relying on biometric data.
To shield against similar breaches, professionals suggest refraining from using eye-tracking techniques for entering confidential details in VR settings when feasible. It is advisable to utilize physical keyboards or other secure input methods for entering passwords and personal information.
The GAZEploit research emphasizes the necessity for robust privacy protocols as VR technology gains broader acceptance. Maintaining a balance between user engagement and data protection will be pivotal with the increased collection of rich behavioral data by these immersive systems.
While Apple swiftly patched this specific vulnerability, this occurrence serves as a reminder that innovative threat avenues may continue to surface with the advancement of VR/AR capabilities.
The article “New GAZEploit Attack Let Hackers Capture Keystrokes from Apple Vision Pro” was originally published on Cyber Security News.