Oracle WebLogic Server functions as an application server primarily tailored for the development, deployment, and management of enterprise applications following Java EE and Jakarta EE standards.
It plays a pivotal role within Oracle’s Fusion Middleware, offering a dependable and scalable environment.
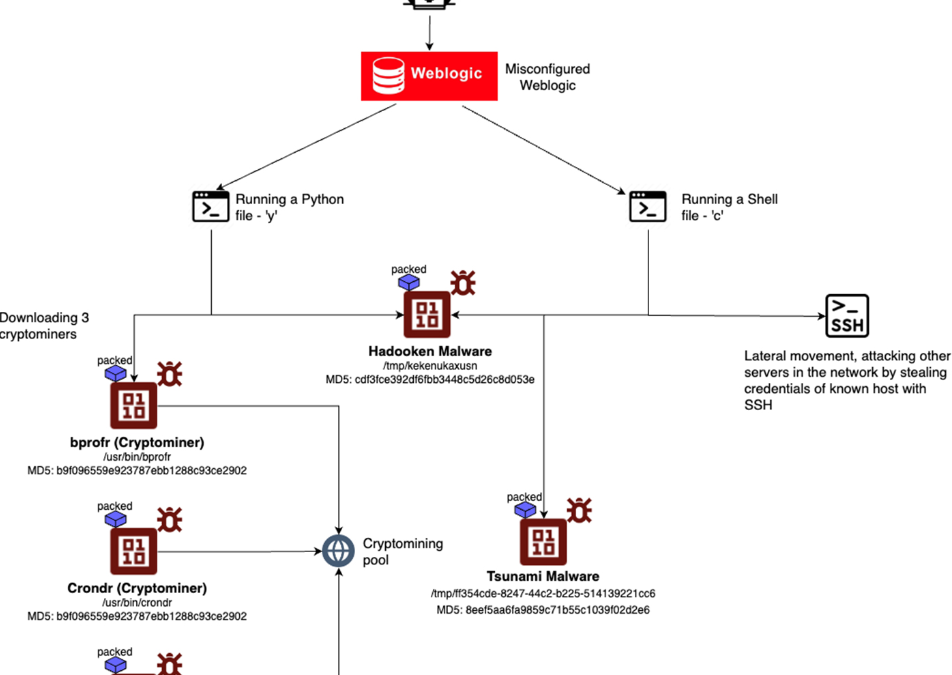
Recent findings from Aqua Nautilus researchers unveiled the existence of a new Linux malware named “Hadooken” actively targeting Oracle WebLogic servers.
Exploitation of Weblogic Servers by Linux Malware
The infiltration of Oracle WebLogic servers by the Hadooken malware involves the exploitation of weak admin credentials as the initial point of entry.
There are two essential components deployed, both listed below:-
- A cryptominer (MD5: 9bea7389b633c331e706995ed4b3999c)
- Tsunami malware (MD5: 8eef5aa6fa9859c71b55c1039f02d2e6)
This attack method employs shell (‘c’) and Python (‘y’) scripts to download and execute payloads, showing a preference for non-persistent locations such as /tmp.
The cryptominer gets placed as ‘/usr/bin/crondr’, ‘/usr/bin/bprofr’, and ‘/mnt/-java’, while Tsunami adopts a random filename within /tmp.
For maintaining persistence, cron jobs are established in /etc/cron.<Period>/<Random String> at varying frequencies.
For lateral movement, SSH data is sought in various directories. The malware resorts to evasion tactics like base64 encoding, log clearance, and process masquerading.
IP addresses 89.185.85.102 and 185.174.136.204 are linked with potential ransomware distributions (Mallox MD5: 4a12098c3799ce17d6d59df86ed1a5b6, RHOMBUS, NoEscape).
An associated PowerShell script ‘b.ps1’ (MD5: c1897ea9457343bd8e73f98a1d85a38f) facilitates the distribution of Mallox ransomware, indicating a cross-platform attack approach.
Interestingly, Shodan uncovers more than 230K internet-connected WebLogic servers, with numerous exposed admin consoles prone to exploitations.
Below, we present the MITRE ATT&CK framework:-
Countermeasures
Here, we outline all the defensive actions:-
- Employ IaC scanning tools for identifying misconfigurations prior to deployment.
- Utilize CSPM tools for scanning cloud configurations to mitigate potential risks.
- Conduct scans on Kubernetes clusters to remediate misconfigurations.
- Secure container images and Docker files.
- Keep a hawk-eye on runtime environments.
Indicators of Compromise (IOCs)
The post New Linux Malware Exploiting Oracle Weblogic Servers appeared first on Cyber Security News.