ANY.RUN enhanced its sandbox for analyzing malware by introducing a novel, private AI model, which supersedes the past publicly available ChatGPT-powered aide.
The novel model exclusively operates on the proprietary infrastructure, enabling paying customers (Hunter and Enterprise plans) to utilize AI insights for private analysis sessions.
It guarantees the confidentiality of user data during AI-driven examination of files and links within the Sandbox environment by granting users the ability to securely inspect sensitive data while benefiting from AI-assisted investigative support.
A sandbox for malware analysis now features an AI assistant to streamline investigations. By selecting the “AI” option adjacent to processes, events, and other items, users can create AI-generated reports, offering in-depth insights on the specific behavior of each item within the analysis session.
This functionality is designed to enhance analysts’ comprehension of malicious actions by providing real-time synopses and highlighting dubious behaviors, leading to expedited and more effective investigations.
The AI assistant scrutinizes process behavior and command line inputs to identify probable security risks by examining the process hierarchy to detect suspicious activity and delivers summaries of each process, enabling users to concentrate on crucial areas.
The assistant inspects the entries on the command line for signs of malicious activity and creates a comprehensive report to aid in investigations.
Suricata regulations serve as digital guards, persistently monitoring network traffic for suspicious activities. When a regulation is triggered, an AI assistant furnishes an elaborate explanation, translating technical terms into simple language.
This enables users to grasp the potential threat level and implement appropriate countermeasures. By providing contextual insights, the AI assistant enhances the efficacy of Suricata’s intrusion detection capabilities.
While vigilantly monitoring network traffic, the assistant meticulously inspects HTTP requests for any abnormal patterns that may indicate malicious conduct.
It also tracks alterations in the system registry, flagging any irregularities that might hint at a malware intrusion.
By proactively identifying and scrutizing these suspicious behaviors, the assistant aids in safeguarding the network from potential threats.
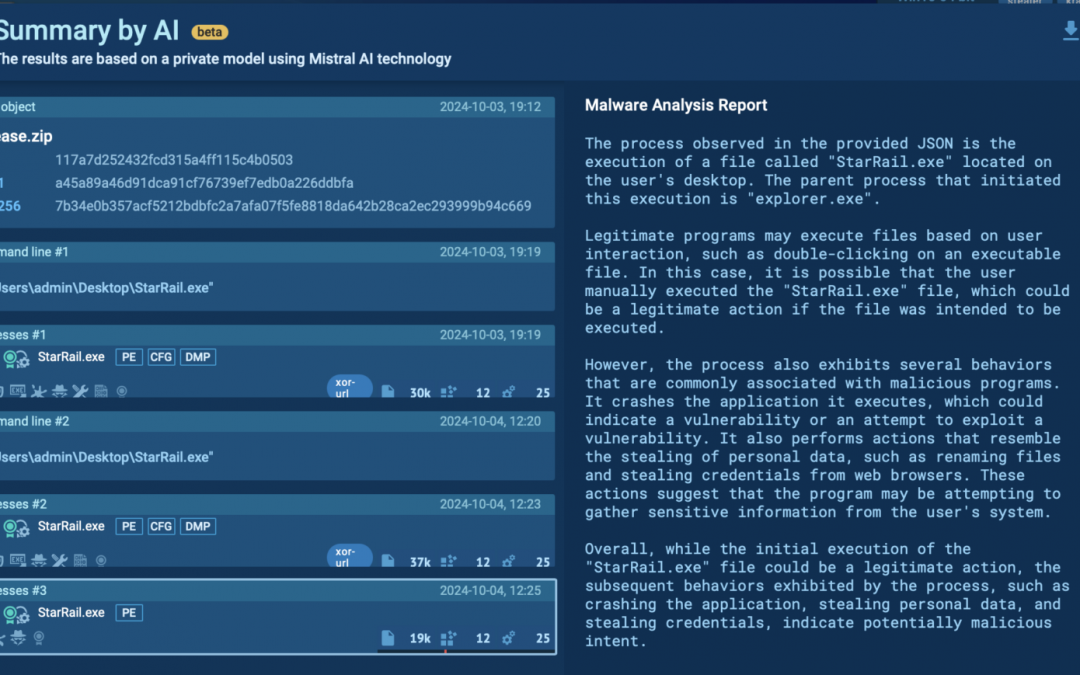
As specified in the AI Summary functionality delicately streamlines malware analysis by consolidating AI-generated reports in one central location.
Located in the upper right corner of the sandbox session, this feature aggregates AI evaluations for processes, Suricata regulations, and other analyzed items.
Activation of the AI Summary function provides an encompassing overview of the analysis, enabling users to efficiently review and comprehend all AI-detected threats and behaviors within the isolated environment.
The private mode of the AI assistant enables users to utilize AI-driven features like summarization, insights, and explanations without compromising the security of their sensitive information.
By functioning in a discreet setting, the AI assistant assures that user data stays confidential and shielded from unauthorized access, which is especially advantageous for users who necessitate a high level of data privacy while still taking advantage of the advanced capabilities of AI technology.
The post Dive into Sophisticated Malware Using ANY.RUN’s AI Assistant Powered by ChatGPT first appeared on Cyber Security News.