Thieving malware is a form of malicious program crafted to breach computers and extract confidential data.
Upon installation, it establishes connection with a command-and-control server managed by cybercriminals, allowing for data theft such as stored passwords and browser cookies.
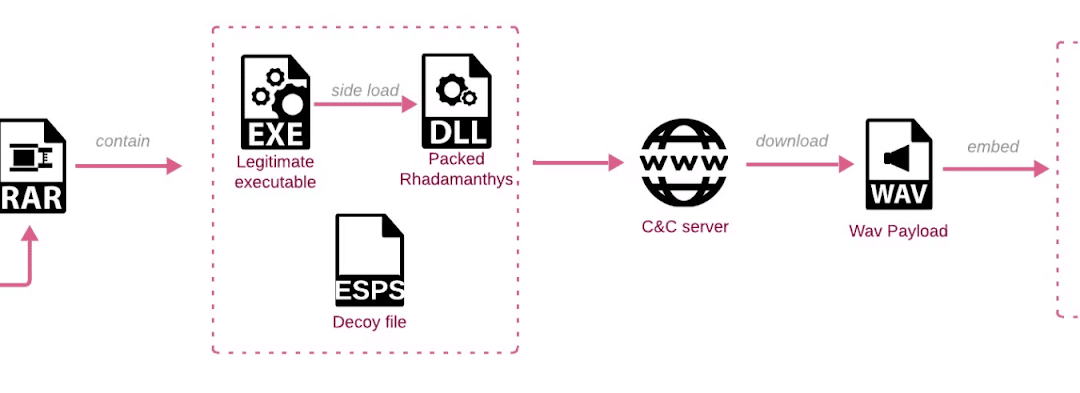
Recently, security specialists at CheckPoint issued a caution about counterfeit copyright claims that spread Rhadamanthys snatcher malware.
An extensive phishing operation dubbed as “CopyRh(ight)adamantys,” is actively utilizing spam and a weaponized malware named “Rhadamanthys Snatcher”, capable of filching sensitive data from the victims’ machines.
The culprits behind this operation have shifted their approach by masquerading as numerous legit entities and falsely accusing the targets of copyright violation on their personal social media platforms like Facebook.
In order to execute this plan, the wrongdoers create Gmail accounts allegedly belonging to attorneys of the dummy corporations, and these emails are specifically customized for each target.
These emails assert that the recipient has violated the company’s brand and insist on the removal of specific images and videos.
It utilizes advanced features, such as engines fueled by artificial intelligence. However, certain sources have not detected any AI-based systems within the malware, suggesting that it employs traditional machine learning techniques commonly found in OCR software applications.
Furthermore, the individuals behind this operation might be utilizing AI to create numerous Gmail accounts for sending seemingly self-composed phishing emails aimed at specific local or English-speaking targets.
However, there are occasional errors, like one email intended for an Israeli individual was mistakenly written in Korean instead of Hebrew, with only the victim’s name localized correctly.
To thoroughly analyze this phishing operation, Check Point Research aims to raise awareness and aid organizations in mitigating this sophisticated danger.
This menace aims to exploit entities and individuals in various regions and industries but primarily targets organizations in the “entertainment,” “media,” “technology,” and “software industries.”
In this scheme, Rhadamanthys malware has impacted organizations across several regions:
- The United States
- Europe
- The Middle East
- East Asia
- South America
The researchers’ evaluation indicates that this is probably the work of a threat group and not an initiative by a nation-state actor, given the operation’s broad reach and utilization of off-the-shelf malware, pointing towards financial motives of the culprits.
Companies engaged in copyright-related activities and their email addresses have reportedly been utilized in numerous phishing scams, increasing the likelihood of attackers impersonating these companies.
Current observations pertain to targets in CheckPoint’s client niche, but the sheer volume of fake emails suggests this may be a fraction of a larger scheme with severe ramifications.
It is advised that enterprises deploy comprehensive security solutions to counter evolving phishing assaults by offering extensive protection against attack strategies and file formats.
The article “Beware of Fake Copyright Claims That Deliver Rhadamanthys Stealer” was originally published on Cyber Security News.