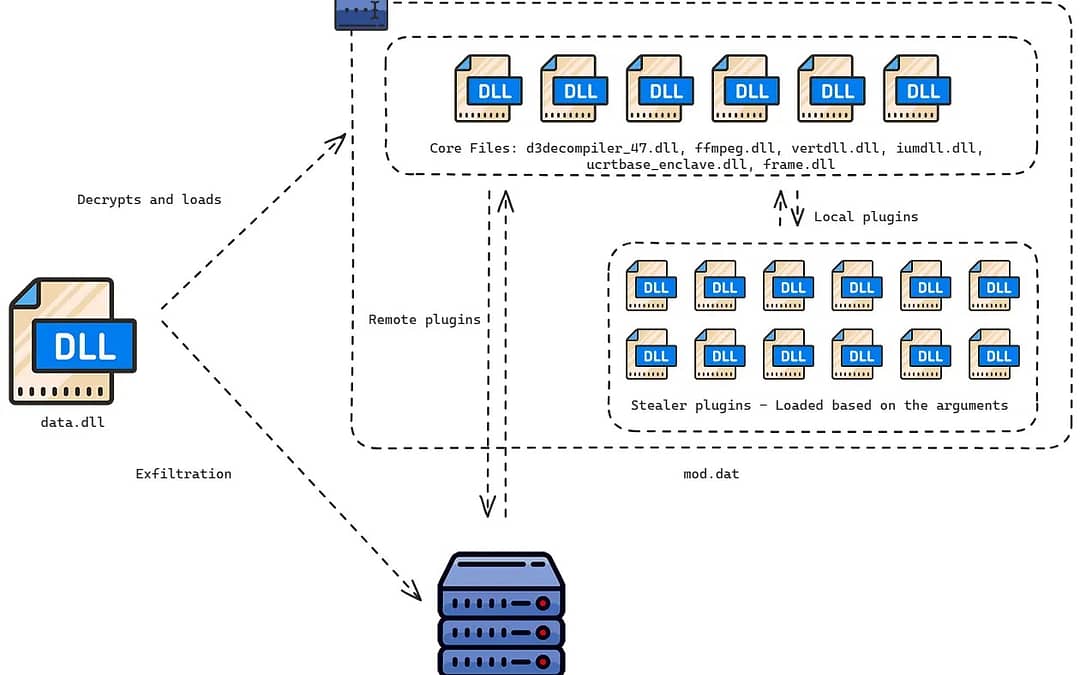
An advanced cyber surveillance campaign carried out by an individual known as BrazenBamboo. This group is leveraging an unpatched flaw in Fortinet’s FortiClient VPN program for Windows to pilfer user logins, within a wider assault using a modular malicious software framework called DEEPDATA.
The recently discovered vulnerability, unveiled in July 2024, enables intruders to extract VPN logins from the memory of FortiClient processes. This gap impacts even the newest edition of FortiClient (v7.4.0) accessible during the discovery period.
BrazenBamboo is assumed to be a Chinese state-linked individual running malicious programs such as DEEPDATA, DEEPPOST, and LIGHTSPY.
The DEEPDATA framework includes a loader (data.dll) and various plugins devised to retrieve sensitive details from breached Windows systems.
The exploitation of FortiClient is executed through a plugin labeled “msenvico.dll,” which extracts usernames, passwords, remote gateways, and ports from JSON entities in the VPN client’s memory.
This method bears resemblance to a comparable vulnerability found in 2016, albeit the current exploitation impacts newer FortiClient editions.
DEEPDATA’s capabilities surpass credential theft, covering the gathering of data from prominent messaging platforms, browsers, and email applications. The malicious software can also capture audio, record keystrokes, and siphon off files from infected devices.
In Volexity’s evaluation, it’s evidenced that BrazenBamboo maintains an intricate structure for command and control (C2) operations. The individual uses several servers for hosting malicious payloads and management software, with data indicating ongoing enhancements of their instruments.
The analysts ascertain with moderate assurance that BrazenBamboo likely serves as a private business producing capabilities for government agents concentrating on domestic objectives. This judgment is based on the terminology employed in C2 infrastructure, design choices in malware development, and the sustained operation despite public exposure.
Volexity informed Fortinet of the FortiClient flaw on July 18, 2024, and Fortinet recognized the issue on July 24, 2024. Nonetheless, by the time of Volexity’s communication (November 2024), the problem remains unsolved, and no CVE identifier has been allocated.
The identification of this campaign underscores the ongoing threat presented by well-equipped APT organizations and the urgency of swift patch application. Businesses utilizing FortiClient VPN are encouraged to stay alert for updates from Fortinet and introduce supplementary security measures to safeguard sensitive logins.
Given the evolving threat landscape, cybersecurity specialists need to stay watchful against sophisticated offenders like BrazenBamboo, who showcase the adeptness to capitalize on zero-day vulnerabilities in broadly used security programs.
The article BrazenBamboo APT Exploiting FortiClient Zero-Day to Steal User Credentials was first seen on Cyber Security News.