Tools for Vulnerability Management play a key role in identifying, examining, and addressing vulnerabilities in web and network-based applications. The frequently used terms in the security domain include vulnerability, risk, and peril.
Risk refers to the likelihood of harm or loss, while a threat is an unfavorable occurrence that exploits a vulnerability. Identifying these weaknesses is crucial for safeguarding all assets and the organization’s data. A vulnerability is a flaw or gap in a system that poses a risk.
The primary goal of vulnerability management tools is to pinpoint issues. Many security experts and businesses leverage the Common Vulnerability Scoring System (CVSS) to assess vulnerabilities based on their severity.
These tools routinely scan the system or network to detect vulnerabilities and outdated software, thus protecting it against both external and internal threats. It encompasses the procedures, strategies, and tools for pinpointing, evaluating, and informing about system or network security vulnerabilities.
Prior to commencing the vulnerability management process, specific steps need to be taken, such as defining the scope, selecting tools for detecting vulnerabilities, assigning roles and responsibilities to the team, and formulating policies and SLAs.
The Vulnerability Management Procedure: Four Crucial Steps
- Spotting Vulnerabilities: – Utilize various vulnerability scanners to inspect the system, connected devices, databases, virtual machines, servers for exposed ports and services to uncover potential security flaws.
- Evaluating Vulnerabilities: – After identifying vulnerabilities, assess them using the organization’s risk scoring system and prioritize actions accordingly.
- Managing Vulnerabilities: Three strategies—Remediation, mitigation, and acceptance—are employed to manage vulnerabilities according to their criticality.
- Notifying about Vulnerabilities: Reporting is fundamental in any evaluation or process. Vulnerabilities that are discovered should be duly documented, outlining steps for replication, impact analysis, and mitigation.
Boosting infrastructure security with vulnerability management solutions enhances usability for individuals and hinders potential attackers from gaining unauthorized access. These tools can reveal vulnerabilities and address them before malicious actors exploit them.
Top 10 Vulnerability Management Tools in 2024 and Their Features
- Intruder: Automated vulnerability scanning tool with proactive surveillance and cloud-based security insights.
- Qualys: Extensive cloud-based platform for ongoing vulnerability management and adherence to standards.
- Acunetix: Proficient in web security scanning with precise detection and reporting capabilities.
- Tripwire: Offers robust security setup management and monitoring of file integrity.
- Astra Pentest: Provides continuous vulnerability assessments with detailed reports and actionable remediation instructions.
- Rapid7: Unified platform for managing vulnerabilities, detecting issues, and responding to incidents.
- Syxsense: Integrates endpoint management with real-time vulnerability identification and patching.
- F-Secure: Provides proactive vulnerability scanning and threat intelligence to enhance security measures.
- OutPost24: Scalable network security evaluation with continual monitoring capabilities.
- BreachLock: Cloud-native platform offering AI-driven vulnerability scanning and penetration testing services.
Top Features of Vulnerability Management Software in 2024
| Vulnerability Management Tools | Key Points | Unique Attribute | Pricing | Free Trial / Demo |
|---|---|---|---|---|
| 1. Intruder | 1. Proactive detection of emerging threats 2. Monitoring and reduction of attack surface 3. Enhanced cloud security with AWS, GCP, and Azure integrations 4. Identification of assets and network scans5. Guidelines for effective remediation and compliance reporting |
Automated scanning for network vulnerabilities. | Starting at $99 per month | Available |
| 2. Qualys | 1. Management of vulnerabilities2. Discovery and cataloging of assets3. Assessing vulnerabilities4. Integration with patch management | Continuous security monitoring in the cloud. | Pricing varies. Contact for a quotation | Available |
| 3. Acunetix | 1. Scanning for web vulnerabilities2. In-depth scanning capabilities3. Coverage of OWASP Top 104. Scanning networks | Comprehensive testing for web application security. | Pricing varies, get in touch for a quote | Available |
| 4. Tripwire | 1. Management of Configuration,2. Vulnerability Tracking3. Monitoring of File Integrity (FIM)4. Assessment of Security Configurations | Monitoring file integrity and ensuring compliance. | Contact for personalized pricing | Not Provided |
| 5. Astra Pentest | 1. Automated Scanning2. Extensive Scanning Capabilities3. Smart Fuzzing4. Customizable Testing Parameters | Professionally managed pentesting with actionable feedback. | Commencing at $699 per scan | Available |
| 6. Rapid 7 | 1. Managing Vulnerabilities2. Penetration Testing3. Incident Detection and Response4. Application Protection | Dynamic testing for application security. | Commences at $5,775 per month | Available |
| 7. Syxsense | 1. Management of Endpoints | Unified endpoint vulnerability supervision. | Commences at $600 annually | Yes |
| 8. F-Secure | 1. Endpoint Safety 2. Threat Insights 3. Emergency Response and Investigation 4. Vulnerability Control |
Advanced threat identification and action. | Pricing determined by required solutions | No |
| 9. OutPost24 | 1. Vulnerability Control 2. Web App Secureness 3. Net Security 4. Cloud Safety |
Flexible vulnerability oversight and evaluation. | Reach out for pricing specifics | Yes |
| 10. BreachLock | 1. Vulnerability Evaluation 2. Pen Testing 3. Web App Evaluation 4. Net Security Evaluation |
Penetration assessment as a utility (PTaaS). | Personalized pricing is accessible upon demand. | Yes |
1. Intruder
Intruder brings together persistent network watch, automated vulnerability scrutiny, and proactive menace handling within a solitary framework. This methodology delivers an intricate perspective of your strike terrain, allowing you to rectify the most vital weaknesses quickly and efficiently.
Intruder evaluations can showcase your commitment to protection to associates and customers or meet the requirements of ISO 27001 and SOC 2. Furthermore, the Cyber Hygiene Score from Intruder traces the duration taken to rectify concerns and assesses how you measure up to sector benchmarks.
You can seamlessly blend Intruder with your cloud vendors (AWS, Azure, Google Cloud), receive preemptive notifications when uncovered ports and amenities alter throughout your digital assets, and automatically survey your systems when any alteration occurs.
Characteristics
- Precautionary surveys for emerging dangers
- Examination and reduction of assault territory
- Efficient cloud protection with AWS, GCP, and Azure associations
- Discovery of possessions and network sweeps
- Pragmatic remediation guidance and adherence accounts
| What Stands Out? | Ways to Improve? |
|---|---|
| Detailed checks and surveys that are conducted proactively | Added features like bug exploration are solely accessible in the Premium and Vanguard schemes. |
| Skilled team of infiltration examiners | Enhanced incorporation with a wider assortment of tools. |
| Uncomplicated to utilize and user-friendly design | Augmented user interface styling. |
| Diverse developer integrations with platforms such as Jira, Slack, GitHub, and more | Faster surveying and reporting periods. |
| Exceptional and responsive customer support unit | |
| Displays resources that are exposed on the web | |
| Automation of compliance & first-rate reports |
2. Qualys

Qualys, a vulnerability management tool, identifies all environmental assets and assesses risk across vulnerabilities, support, and asset categories for proactive risk mitigation. It lets firms easily catalog software, hardware, and unmanaged network assets and mark key assets.
This tool is compatible with patch management solutions and configuration management databases (CMDBs), allowing for fast vulnerability discovery, prioritization, and automated, scalable remediation of vulnerabilities to reduce risk.
All of the discovered hardware, including databases, servers, and networking components, is automatically classified by Qualys. It also records the software, services, and traffic installed on the system, along with their current running states.
Characteristics
- With Qualys’ vulnerability management tools, you can find and rank vulnerabilities in networks, systems, and apps.
- With Qualys, businesses can find and list all of their IT assets.
- It has tools for continuous monitoring that let you always see how secure your IT assets are.
- It helps businesses make sure they are following security rules and industry laws.
- Finds security holes in old systems automatically.
- Check and understand danger across all of your networks automatically.
- Assessment of the security of a multi-cloud system.
| Highlights | Areas for Enhancement |
|---|---|
| Swiftly resolve threats at a large scale. | Most features necessitate a license. |
| Manage asset vulnerabilities throughout the complete vulnerability lifecycle. | Acquisition of scan results may be time-consuming. |
| Jubilant user interface and data precision. | Inadequate customer assistance. |
| Minimized false positives owing to cloud agents. | The mobile endpoint lacks clarity compared to the cloud endpoint. |
3. Acunetix
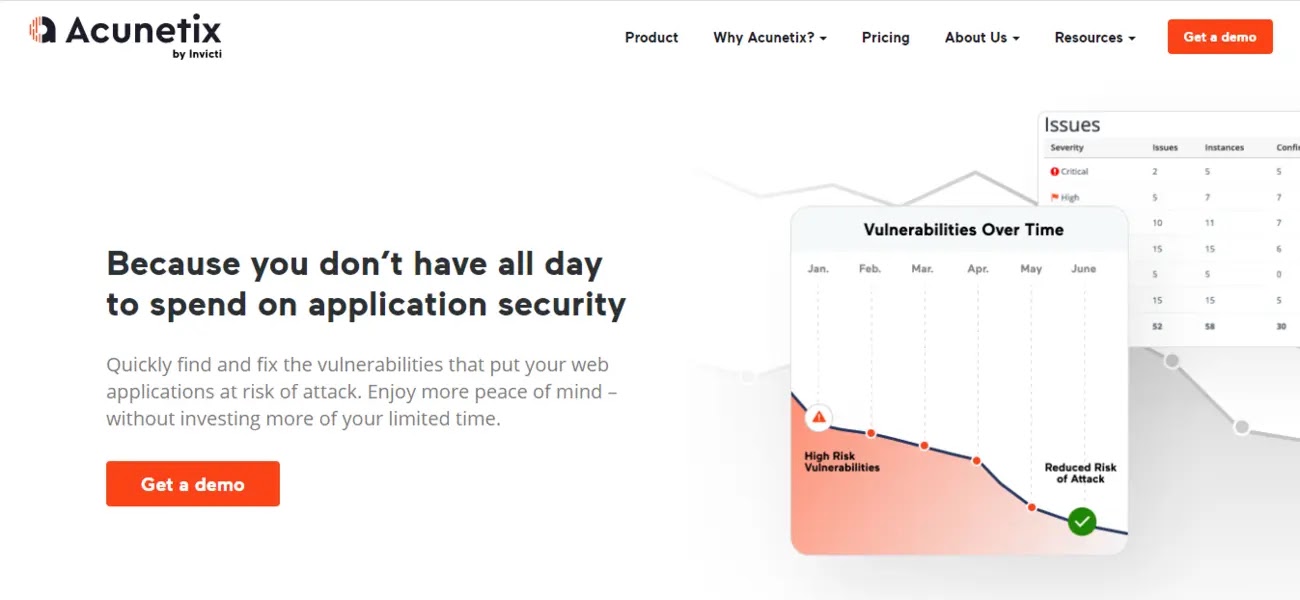
Acunetix is a robust vulnerability management software that specializes in web application security. It provides automated scanning to identify and address a broad spectrum of vulnerabilities, such as SQL injection, XSS, and other web-based risks.
The tool offers comprehensive vulnerability reports and seamlessly integrates with popular development and CI/CD tools, enabling organizations to detect and resolve security weaknesses early in the development process, thereby improving overall security measures.
Acunetix caters to both on-premises and cloud deployments, providing flexibility and scalability for enterprises of all sizes. Its user-friendly interface and extensive dashboard streamline vulnerability management, making the process efficient and simple.
Characteristics
- The software automatically scans websites and web apps for security vulnerabilities.
- Advanced testing techniques are employed by Acunetix to identify vulnerabilities comprehensively.
- Acunetix detects vulnerabilities in web applications listed in the OWASP Top 10 and the CWE/SANS Top 25.
- These lists are widely recognized industry standards for web application security.
- Acunetix’s network scanning tools can identify network-based vulnerabilities and interconnected devices.
- Once a vulnerability is discovered, Acunetix adds it to the list and marks it as “Open.”
- It verifies the resolution of identified vulnerabilities through retesting.
- The tool creates macros that can automatically scan password-protected areas.
| Advantages | Areas for Improvement |
|---|---|
| Rapid scanning of multiple domains. | Instability noted in certain tool versions. |
| Identification of over 7,000 vulnerabilities, including zero-day threats | Limited configuration options for scans. |
| Scheduling of daily, weekly, and monthly scans. | Challenges with pre-recorded login sequence specifications. |
| Straightforward setup and configuration process initially. | Lack of support for multiple endpoints. |
4. Tripwire

Tripwire Vulnerability Management Software delivers continuous monitoring and evaluation of your IT environment to pinpoint vulnerabilities across servers, networks, and cloud infrastructures. This enables organizations to prioritize and resolve risks efficiently.
The tool seamlessly integrates with existing security mechanisms to provide actionable insights, allowing security teams to concentrate on high-priority vulnerabilities and ensure compliance with industry standards and internal security guidelines.
Tripwire’s solution includes automated patch management and configuration controls, reducing the attack surface while preserving system integrity. This makes it a crucial component of a holistic cybersecurity approach.
| Advantages | Areas for Improvement |
|---|---|
| Strong technical support. | Unimpressive technical support. |
| Utilization of advanced vulnerability scoring methods. | Generates unnecessary network traffic. |
| Minimal impact on the network. | Inconsistencies in some vulnerability findings. |
| Customized reporting based on the audience. | Somewhat lacking in vulnerability tracking. |
5. Astra Pentest

Astra Pentest, alongside manual pen testing, serves as an advanced automated vulnerability management tool that assesses and highlights asset vulnerabilities.
In addition to over three thousand automated and manual pentests, the platform verifies assets for essential vulnerability issues (CVEs) listed in the OWASP top ten and SANS 25. It encompasses every necessary test to comply with GDPR, HIPAA, and ISO 27001 standards.
Administrators can monitor and manage vulnerabilities effortlessly using the no-code dashboard. The vulnerability risk scores are determined by the CVSS score, potential losses, and overall corporate impact. Examinations for ISO 27001, SOC 2, PCI-DSS, HIPAA, and GDPR compliance are available.
| Advantages | Areas for Improvement |
|---|---|
| Integration with CI/CD platforms, Slack, and Jira. | Limitation in available integration options. |
| Optimization for return on investment (ROI). | Potential incapability to detect certain malware attacks that go unnoticed. |
| Precise risk scoring and comprehensive remediation guidelines. | Reliance on external dependencies, i.e., manual pentesting. |
| Excellent, quick, and thorough support. |
6. Rapid 7

Rapid 7 InsightVM and Nexpose, an on-premise vulnerability scanner, address vulnerabilities efficiently. By amalgamating various security technologies, Rapid 7 empowers teams to automate processes, monitor the network, manage vulnerabilities, analyze and thwart threats, and more.
Nexpose aids in minimizing threat exposure by prioritizing risk across configurations, controls, vulnerabilities, and real-time change assessments. Regarding pen-testing applications, Rapid 7 is a valuable choice due to its comprehensive features and capabilities.
is your safest bet.
Nexpose streamlines asset categorization by remediation responsibility and facilitates the generation of remediation reports for asset teams—Coalesced Reconnaissance, Payload, and Closure functionalities in a unified application.
| What Qualifies as Admirable? | What Areas could Benefit from Improvement? |
|---|---|
| Monitor and convey the progress efficiently. | Regular updates and system freezes. |
| Seamless implementation of RESTful API. | Scheduling might turn chaotic if not closely supervised. |
| Integration with over 40 technologies. | Scan with Credentials cannot be personalized or prioritized. |
| Advanced remediation, tracking, and reporting capabilities. | The agent addresses fewer compliance concerns. |
| Extensive range of templates for asset scanning. | The tool lacks a real-time threat protection module. |
7. Syxsense

Syxsense stands out as a premium vulnerability management solution due to its capability to visualize and comprehend each endpoint in the cloud, on-site, or within any other network or location. Leveraging artificial intelligence and industry knowledge, it oversees and defends endpoints by detecting and neutralizing threats.
Syxsense guarantees security through managed services, round-the-clock coverage, and compliance. By enabling patch management and vulnerability scanning, it helps businesses synchronize cybersecurity with IT governance.
Syxsense simplifies remote computer connections without necessitating approval, catering to non-technical individuals. By implementing dynamic searches, it prioritizes device groups and solutions to suit organizational requirements. These attributes may be adjusted by system configurations, severity, risk, and impacted operations.
| What Qualifies as Admirable? | What Areas could Benefit from Improvement? |
|---|---|
| Zero Trust elements are merged into Syxsense. | Remote control tools can be unreliable over slower connections. |
| Simplified connectivity to a user’s device remotely. | Transitioning between monitors is not seamless. |
| No manual uploads required for updates. | Oftentimes encounters duplicate device IDs for end-user systems. |
| Straightforward software packaging. | A gap in patch assessment and deployment. |
8. F-Secure
F-Secure, now known as Secure, emerges as a robust and user-friendly vulnerability management tool. It presents an all-in-one vulnerability evaluation and management platform that offers lucid, actionable, and prioritized insight into threats, backing organizations’ security strategies.
Shield yourself against contemporary attacks and ransomware using this cloud-centric software. It amalgamates automatic patch management, continuous behavioral analytics, vulnerability management, and dynamic threat intelligence.
The tool can check for vulnerabilities round the clock and notify users. Harnessing JSON and HTTP methods such as GET, PUT, POST, and DELETE, the F-Secure Elements Vulnerability Management API is employed.
| What Qualifies as Admirable? | What Areas could Benefit from Improvement? |
|---|---|
| Real-time defense capabilities. | It lacks protection against zero-day threats or forensic analyses. |
| Scalability as the system expands over time. | Insufficient ready-made templates for compliance checks. |
| Automated and tailor-made reports. | Occasionally overly blocks executables, leading to system slowdown. |
| Scan templates provide a convenient way to save a set of preferences. | Some false positives regarding vulnerabilities exist in the results. |
| Diminished resource consumption with background protection. | Occasionally overly blocks executables, leading to system slowdown. |
9. OutPost24
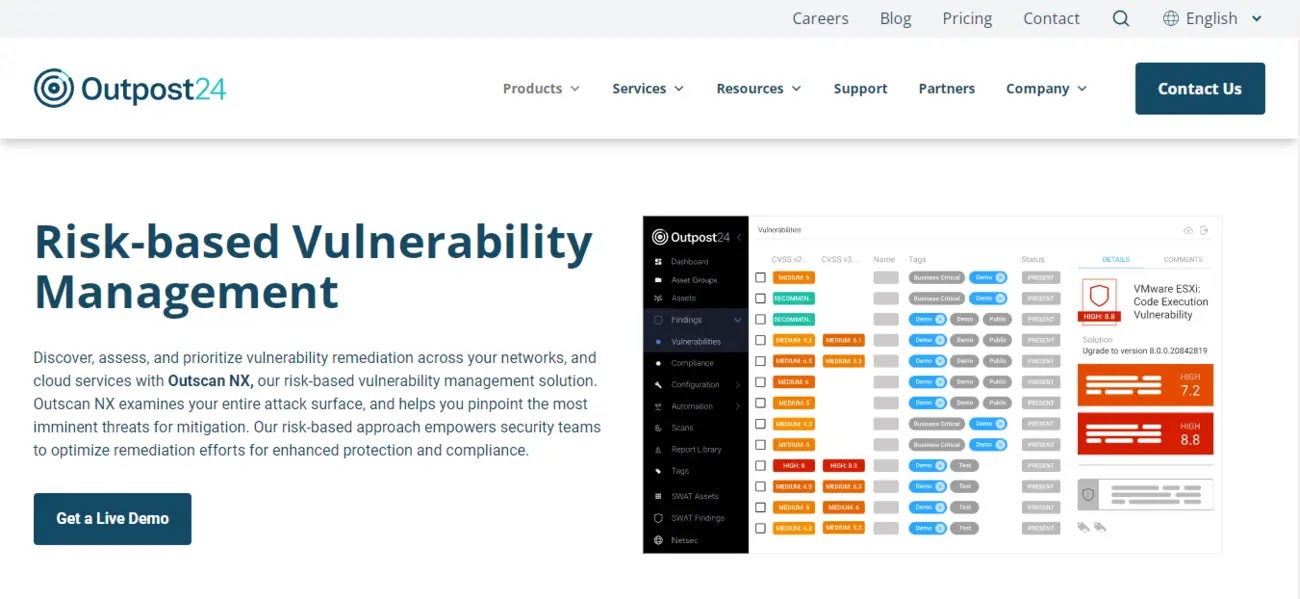
OutPost24 furnishes a consolidated vulnerability management platform that ensures ongoing monitoring, detection, and resolution of security vulnerabilities across networks, applications, and cloud environments, guaranteeing comprehensive defense against potential threats.
The software provides real-time visibility into vulnerabilities, allowing security teams to efficiently prioritize and remediate high-risk issues, thereby reducing the likelihood of breaches and enhancing overall security readiness.
OutPost24 seamlessly integrates with existing security utilities, enabling automated workflows and streamlined processes that elevate operational efficiency and aid organizations in adhering to industry regulations and standards.
| What Qualifies as Admirable? | What Areas could Benefit from Improvement? |
|---|---|
| Guarantees compliance and streamlined reporting. | GUI, dashboards, and reporting present substantial drawbacks. |
| User-friendly internal vulnerability scanner. | Not user-friendly and necessitates additional maintenance effort. |
| Augments prioritization and focused remediation. | Reports contain numerous false positives. |
| Risk-centric vulnerability management solution. |
10. BreachLock

BreachLock provides a cloud-based vulnerability management solution that merges automated scanning with manual penetration tests, offering comprehensive insights into security vulnerabilities and furnishing actionable remedial measures to elevate an organization’s security posture.
The software smoothly integrates with current workflows and utilities, delivering continuous monitoring and real-time reporting, empowering security teams to promptly pinpoint, prioritize, and resolve vulnerabilities across their IT framework.
BreachLock accentuates usability and scalability, making it suitable for businesses of varied sizes. Simultaneously, its AI-driven platform ensures precise identification of vulnerabilities with minimal false alarms, boosting overall efficiency.
| What Qualifies as Admirable? | What Areas could Benefit from Improvement? |
|---|---|
| Rapid, scalable, and efficient. | Needs improvements in support services. |
| Diverse array of educational resources. | Hidden charges associated with using different functionalities. |
| Integration with Jira and robust reporting capabilities. | The product requires enhanced resilience. |
| Diverse array of educational resources. | Need to upscale security thresholds. |
| Managed service offerings. | |
| Compliance management. |
The post 10 Best Vulnerability Management Tools In 2024 appeared first on Cyber Security News.

