A novel form of breach, named “DaMAgeCard,” capitalizes on the SD Express standard to gain direct entry to a device’s memory through its SD card reader.
This technique sidesteps conventional security measures, enabling intruders to retrieve confidential information or introduce harmful code without needing to physically access the internal components of the device.
The advent of the SD Express standard, aimed at amplifying the velocity of data transmission in SD cards, unintentionally uncovers a fresh avenue for cyber intrusions.
Differing from its forerunners, SD Express cards are capable of functioning in both SDIO mode and as a PCIe/NVMe device, empowering them to directly engage with the system’s memory bus. Although this feature boosts efficiency, it concurrently introduces substantial security hazards when not meticulously managed.
Exploring the Methodology of the DaMAgeCard Assault
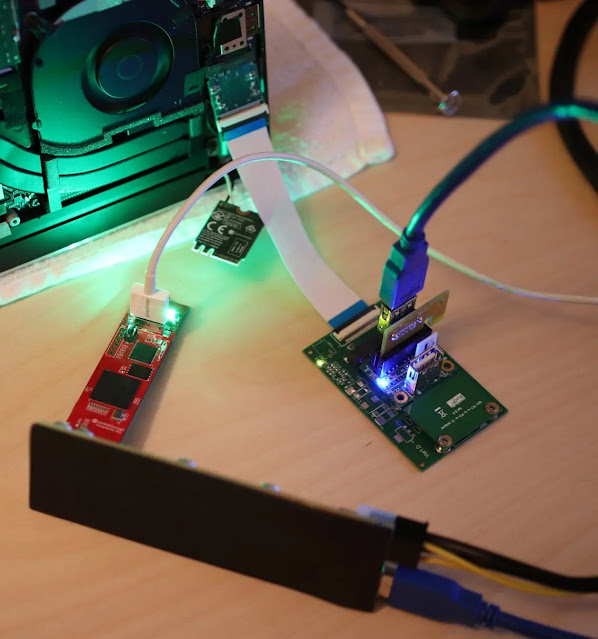
Exploiting the faculty of SD Express cards to transition between SDIO and PCIe modes, the attack commences when an SD Express card is slotted in, prompting the host controller to initially operate in SDIO mode and subsequently switch to PCIe mode upon verifying the capabilities of the card.
Positively Labs researchers demonstrated that by replicating this mode-shifting engagement, they could deceive the host controller into permitting a malevolent device to access the system’s memory.
This feat was accomplished by employing a Raspberry Pi Pico to simulate the requisite signals, eliminating the necessity for an actual SD controller.
The repercussions of the DaMAgeCard assault are significant. It has the potential to:
- Retrieve confidential data: By directly accessing the memory, intruders can obtain encryption keys, personal information, or any data housed in the RAM.
- Plant malevolent code: Malicious code could be planted into the system, potentially culminating in persistent malware invasions or unsanctioned governance over the device.
- Circumvent security measures: Standard security protocols such as IOMMU (Input-Output Memory Management Unit) could be evaded if not adeptly set up, exposing systems to vulnerabilities.
While certain devices, like the MSI gaming laptop scrutinized by researchers, implement IOMMU to curtail memory access, many systems do not activate this protection by default. This lapse places numerous devices, ranging from gaming consoles to professional workstations, at potential jeopardy.
The SD Express technology, despite its susceptibilities, is gaining popularity due to its substantial velocity advantages. Enthusiasts such as photographers, gamers, and other individuals necessitating rapid data transfers are embracing this technology, potentially leading to its extensive adoption across diverse devices. Nonetheless, this acceptance might inadvertently broaden the exploitability of DaMAgeCard-like ploys.
As technology evolves to satisfy consumer demands for speed and efficacy, it is imperative that security mechanisms advance correspondingly. Manufacturers and developers need to accord due priority to securing these fresh interfaces against such sophisticated assaults to safeguard user data and system robustness.
The article DaMAgeCard: A Novel Attack Leveraging SD Cards to Compromise System Memory was originally published on Cyber Security News.