There has been a recent discovery by security experts of an innovative attack strategy that takes advantage of Microsoft’s UI Automation framework, potentially putting a large number of Windows users at risk.
A security researcher named Tomer Peled, working for Akamai, found a new method that enables attackers to circumvent endpoint detection and response (EDR) systems. This breakthrough gives cybercriminals new opportunities to access sensitive data and manipulate user systems without being detected.
The Vulnerability in UI Automation
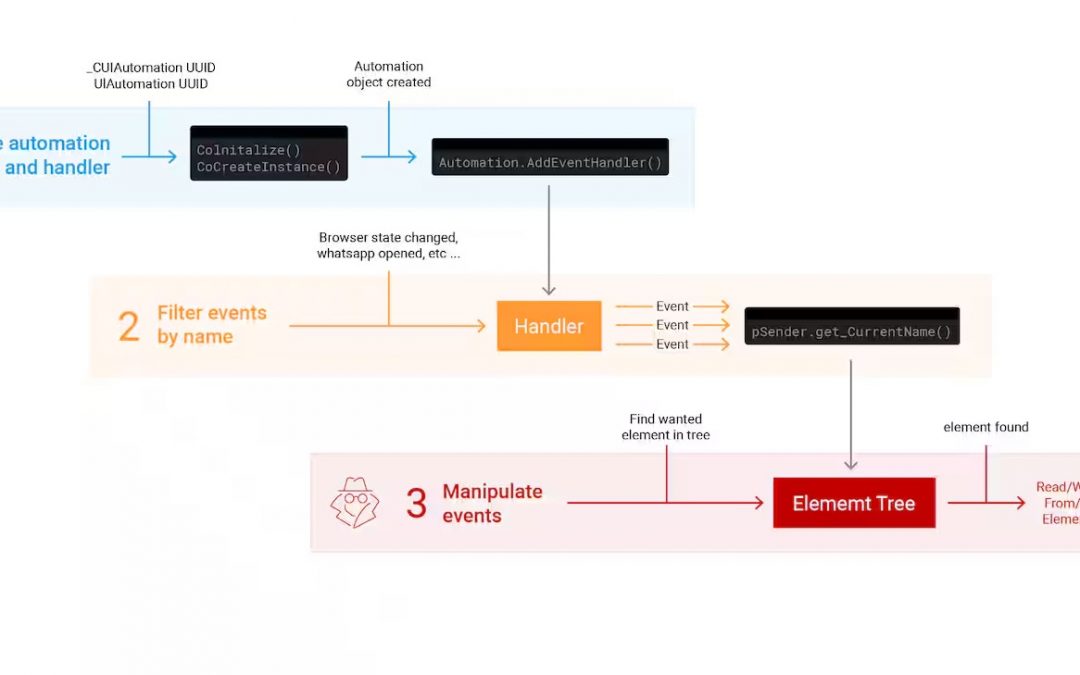
An important security flaw has been identified in the UI Automation framework, which was originally designed to aid users with disabilities.
This framework, which has been part of all Windows operating systems from XP onwards, has elevated privileges for interacting with user interface elements.
Despite its original benign purposes like assisting in text enlargement and screen reading, this functionality can be exploited by malicious actors.
Researchers have illustrated that by convincing a user to launch a program that uses UI Automation, attackers can:
- Steal sensitive data
- Redirection of browsers to fraudulent websites
- Access and deliver messages in popular chat apps like WhatsApp and Slack
- Extract credit card details from web browsers
- Execute commands without being noticed
One of the more harmful methods researchers thought of using the UIA for is the theft of credit card information.
“By setting up a handler to monitor changes in UI elements, an attacker can systematically observe a change when the user enters their credit card information on an online store. The attacker can then retrieve this data to later send it out,”
Undetectable by Present EDR Solutions
Most worryingly, none of the EDR technologies tested could detect any malicious behavior using this method. This invisible mode of attack makes it especially menacing and appealing to potential hackers.
Given that this vulnerability affects all Windows versions from XP up, millions of users may be in jeopardy. Although Microsoft has introduced certain restrictions on UI Automation, adept attackers can still find ways to exploit the features.
Security professionals are pushing for system admins and users to stay alert. Monitoring the usage of UIAutomationCore.dll and looking out for unexpected UI Automation named pipes are suggested as possible detection techniques.
As the cybersecurity field grapples with this emerging threat, it is a stark reminder that technologies developed to aid us can sometimes be turned against us. Efforts are now focused on devising effective defenses against this sneaky but potent attack method.
The post “Hackers Utilize Critical Windows UI Automation Framework Vulnerability to Evade EDR” was originally published on Cyber Security News.