The ASEC Security Intelligence Center has discovered a novel variation of DDoS malware, dubbed cShell, with a focus on inadequately managed Linux SSH servers (screen and hping3).
This malware capitalizes on feeble SSH credentials and utilizes Linux utilities for carrying out complex DDoS assaults. The emergence of this threat underscores the increasing danger posed by malevolent actors exploiting unsecured systems.
Initial Access and Infection Methodology
Through monitoring honeypots, ASEC has identified that attackers are scanning openly accessible SSH services and employing brute force methodologies to gain entry.
Upon infiltration, they execute commands to deploy utilities like curl and a malware variant named cARM.
Depending on the distribution of Linux, installation is carried out using package managers such as apt, yum, or apk. It is worth noting that error notifications during this phase are scripted in German, indicating a potential source or operational insight.
The malware embeds itself within the /etc/de/cARM directory and utilizes a setup file named sshell.service to enroll as a persistent service via the systemctl directive. This ensures the malware’s continuity even post system reboots.
Utilization of Linux Utilities
Differing from conventional DDoS bots, cShell leverages existing Linux tools screen and hping3 to execute its offensives:
- Screen: An application for managing multiple terminal sessions, allowing operations to continue in the background even if the terminal is shut. cShell leverages it to run commands under the session title “concurrent.”
- Hping3: A tool for packet generation and analysis used for network diagnostics. cShell takes advantage of its capability to dispatch TCP, UDP, and ICMP packets for a variety of DDoS attack forms.
The malware installs these utilities using commands like:
# bash -c apt -y install curl && apt -y install hping3 && apt -y install screenSubsequently, it initiates hping3 commands via screen sessions to initiate offensives such as SYN floods, ACK floods, and UDP floods. These attacks submerge the targeted servers by transmitting extensive amounts of packets at the maximum velocity.
Salient Characteristics of cShell
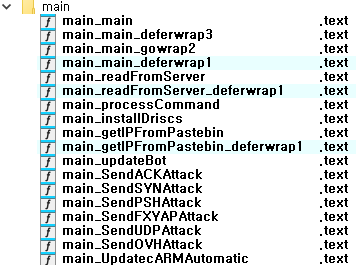
As per the Asec research, Six DDoS directives are integrated into cShell, developed utilizing the Go programming language and encompassing an update function. It receives directives via communication with a command-and-control (C&C) server. Some of the supported commands are:
- SYN Flood:
hping3 -S -d <Data Size> -p <Port> --flood <Target IP> - ACK Flood:
hping3 -A -d <Data Size> -p <Port> --flood <Target IP> - UDP Flood:
hping3 -2 -d <Data Size> -p <Port> --flood <Target IP> - Custom DDoS assaults utilizing flags like
-FXYAP.
The malware also establishes connections to various Pastebin URLs during its update process to retrieve the most recent version using curl. This redundancy guarantees sustained functionality even if certain C&C servers are dismantled.
Guidelines for Safeguarding
System administrators overseeing Linux servers are advised to take preemptive actions to shield against such hazards:
- Select robust, distinctive passwords for SSH accounts and update them on a routine basis.
- Maintain systems up-to-date with the latest security fixes.
- Implement firewalls and other security measures to curb unauthorized entry.
- Supervise server operations for anomalous activity or unauthorized setups.
- Upgrade antivirus solutions such as V3 to proactively thwart malware invasions.
Insufficiently secured Linux systems continue to be prime objectives for assailants aiming to construct botnets for DDoS offensives.
By enforcing rigorous security protocols, administrators can alleviate risks and safeguard their infrastructure against exploitation.
The post New DDoS Malware “cShell” Exploit Linux Tools to Attack SSH Servers appeared first on Cyber Security News.