Deceptive cyber schemes known as phishing attacks involve threat actors masquerading as trusted sources to deceive individuals into disclosing sensitive data such as “passwords” or “financial information.”
These fraudulent activities are conducted through “emails” or “messages” that induce a sense of urgency.
Furthermore, these fraudulent practices often direct victims to “dangerous websites” or “persuade them to download harmful attachments.”
Recent investigations by cybersecurity experts at Sekoia have uncovered that the “Mamba” toolkit is actively exploiting multi-factor authentication to carry out sophisticated phishing attacks.
Mamba Toolkit Exploits Multi-Factor Authentication
In October 2024, cybersecurity researchers unveiled an advanced phishing initiative named “Mamba 2FA.”
This fraudulent campaign targets users of Microsoft 365 through intricate “HTML attachments” that replicate genuine “Microsoft login pages” convincingly.
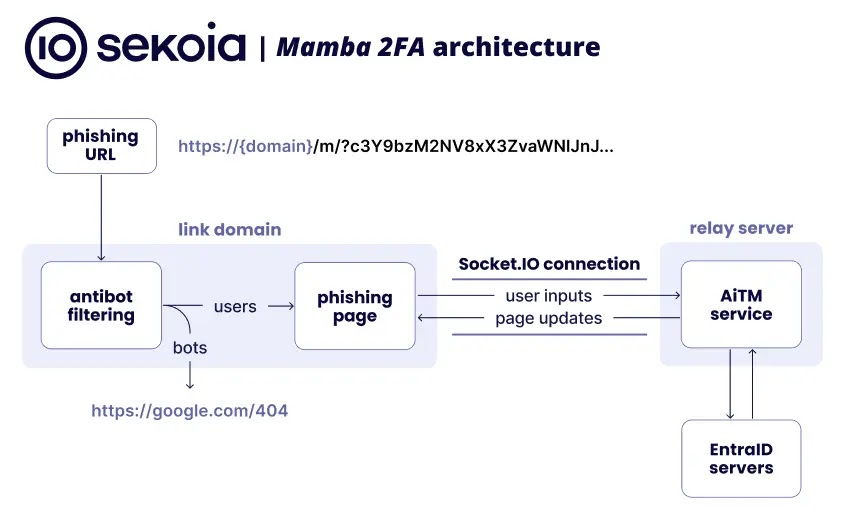
This phishing tool utilizes an “AiTM” method and leverages the “Socket[.]IO” JavaScript library to establish “real-time websocket connections” with backend servers, enabling it to bypass standard MFA safeguards.
The phishing system operates on a “two-tier framework” with URLs following a specific format (https://{domain}/{m,n,o}/?{Base64 string}):-
- Link domains
- Relay servers
The toolkit supports four different phishing page formats, including “OneDrive (o365_#one),” “standard Microsoft sign-in (o365#nom),” “Secure SharePoint Online link (o365#sp),” and “voice message notifications (o365#_voice).”
It is marketed as a “PhaaS platform” for ‘$250 per 30-day subscription’ via Telegram. Customers who opt for this subscription can generate tailored “phishing links” and “HTML attachments” through a dedicated bot.
The HTML attachments are especially sophisticated, containing obscured ‘JavaScript code’ that redirects victims to phishing sites while concealing non-malicious content using ‘CSS,’ thereby enhancing the complexity of detection, as per the Sekoia research.
This service maintains a shared pool of servers and domain names, showcasing its progression from its initial emergence on “ICQ” in November 2023 to its current advanced form targeting “multiple entities” via its “dispersed infrastructure.”
The Mamba 2FA platform offers various features:
- Supports MFA without phishing defenses
- Integrates with Entra ID, AD FS, third-party SSO, and Microsoft accounts
- Dynamically reflects enterprise-specific login branding
- Instantly forwards stolen credentials and cookies through a Telegram bot
- Obstructs access from security scanning services
Link domains are specialized web addresses utilized in sophisticated phishing operations deploying an “anti-bot” detection mechanism to sift out security tools and automated scanners.
When these domains detect potential security solutions, they automatically redirect visitors to a benign page (“https://google[.]com/404”).
For regular visitors, the system delivers a minimal HTML document including vital components (“a Socket.IO JavaScript library (version 4.7.5) for real-time bidirectional communication,” “unique identifiers stored in HTML attributes (with the ‘sti’ attribute containing a double Base64-encoded customer ID, and ‘vic’ attribute storing the target email),” and “template scripts (such as jsdrive.js for OneDrive,” “jsnom.js for Microsoft sign-in,” “jssp.js for SharePoint,” and “jsv.js for voice mail templates)”).
These templates manage the appearance of the phishing page and establish WebSocket connections with relay servers to process user inputs like ’email addresses,’ ‘passwords,’ and ‘MFA codes’ through specific event commands (‘new-session,’ ‘password_command,’ ‘otp_command’).
The system operates response events (‘s2c,’ ‘s2c_cookies,’ ‘s2c_restart’) to regulate page behavior and updates while employing proxy servers to conceal the true source of authentication attempts against Microsoft’s “Entra ID servers,” bolstering the attack infrastructure’s “resilience” and making it more “difficult” to trace.
The post Mamba Toolkit Exploits 2FA In Advanced Phishing Scheme appeared first on Cyber Security News.