ElizaRAT is categorized as a form of malicious software that mainly targets Windows systems and operates as a RAT, allowing unauthorized access to be gained by threat actors on compromised machines.
This malicious software is usually spread through phishing schemes or downloads containing malware.
Recently, researchers at CheckPoint have identified that APT36 hackers have been actively targeting prominent users of Windows devices with ElizaRAT.
The Windows Systems Under Attack by APT36 Group
Known as “Transparent Tribe,” APT36 is an APT group based in Pakistan that conducts sophisticated cyber-espionage campaigns aimed at Indian government and military entities using the Windows RAT named ElizaRAT.
ElizaRAT was first discovered in 2023 and has since evolved significantly by integrating advanced features like:
- Execution of Control Panel (.CPL) files
- Utilization of cloud-based C2 infrastructure (including Slack, channels, Google Drive, and VPS)
The technical structure of the malware involves the implementation of the “.NET” framework with “Costura for assembly embedding,” integration of SQLite database for local data storage, and use of IWSHshell for creating Windows shortcuts.
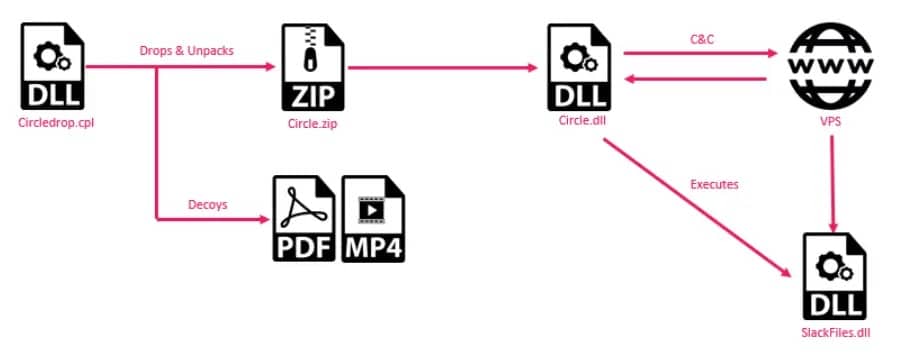
In addition, the infection process of ElizaRAT begins with phishing emails containing malicious CPL files distributed through Google Storage links.
Upon execution, it ensures persistence by generating a unique victim ID, establishing working directories in %appdata%, and deploying additional payloads such as ApoloStealer.
As per the report by Checkpoint, the stealer component of the malware focuses on sensitive file types (.doc, .pdf, .ppt, .xls) for systematic data exfiltration through encrypted channels.
The malware employs advanced evasion tactics like:
- Verification checks for time zone matching India Standard Time
- Ensuring reliability through various C2 communication methods
- Utilizing different C2 communication methods from Slack API calls to Google Cloud Storage authentication via X.509 certificates
Each variant of the campaign demonstrates increasingly sophisticated capabilities while maintaining the primary aim of persistent data theft from targeted Indian institutions. ‘ConnectX’ is a USB-focused malware component within the ElizaRAT system.
It utilizes WMI to monitor system events every 2 seconds, detecting USB drive insertions with the following query:
- SELECT * FROM __InstanceCreationEvent WITHIN 2 WHERE TargetInstance ISA ‘Win32_DiskDrive’
Furthermore, it retrieves files from external drives by collecting device IDs and serial numbers upon detection.
The stolen data is then stored in a ZIP archive within the working directory %appdata%BaseFilteringEngine.
The link between the malware and “Transparent Tribe” is evident through the consistent use of the identifier “Apolo Jones” across various components, like the password “ApoloJones2024” for ZIP compression and function naming in the SlackFiles.dll payload.
.webp)
For command and control infrastructure, along with the deployment of modular payloads like ApolloStealer, the malware integrates with major cloud services (Google Drive, Telegram, Slack), showcasing the increasing sophistication of the threat actor in cyber espionage operations.
The post APT36 Group Targeting Windows Systems through Google Drive & Slack Abuse appeared first on Cyber Security News.