
Cyber Security
“`html AWS Power Outage On March 1, 2026, a significant power interruption in the AWS me-central-1 (Middle East) region was triggered by an unusual physical occurrence where external objects collided with a data center, igniting sparks and a fire. This incident...

Cyber Security
“`html A significant zero-interaction flaw in OpenClaw, one of the swiftly expanding open-source AI agent frameworks, has been identified by Oasis Security experts, enabling any harmful website to quietly take complete command of a developer’s AI agent...

Cyber Security
“`html The U.S. administration has executed extraordinary measures against the domestic AI enterprise Anthropic, instructing every federal department to promptly halt the usage of its AI model Claude and formally classifying the organization as a supply chain...

Cyber Security
“`html A significant privilege elevation flaw impacting Google Cloud API keys reveals that legacy public-facing keys now unobtrusively provide unauthorized access to Google’s Gemini AI endpoints, compromising private files, stored data, and billable AI usage to...
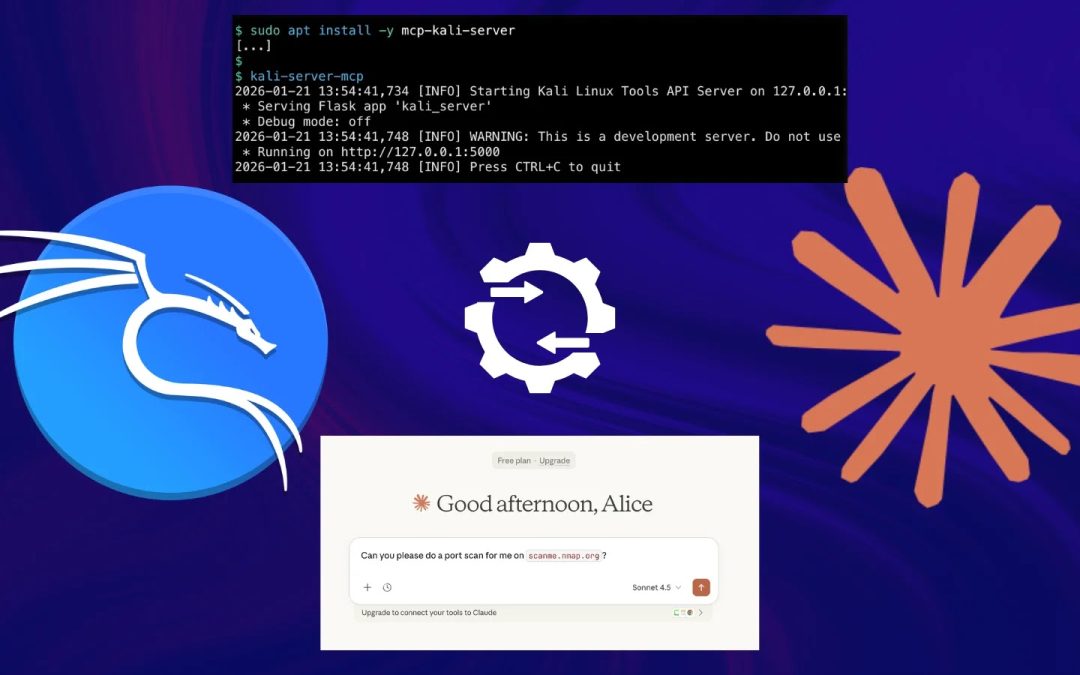
Cyber Security
“`html Kali Linux Integrates Claude AI Kali Linux has officially launched a built-in AI-supported penetration testing workflow, allowing security experts to issue commands in natural language via Anthropic’s Claude AI, which are subsequently converted into live...






