Cyber Security
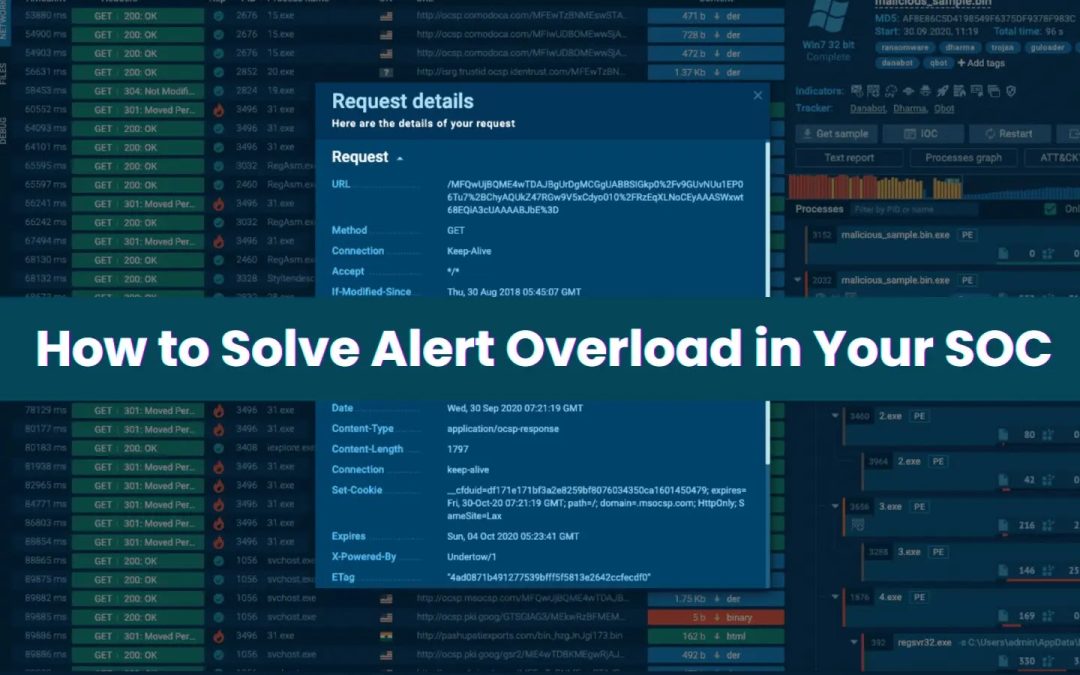
“`html Your SOC produces numerous alerts each day. A significant portion of these are minor, repetitive, or erroneously triggered. While this may appear to be a technical dilemma, it is fundamentally a business challenge. Each Alert Has a Cost When analysts are...

Cyber Security
“`html Cloudflare issued a detailed report explaining the origins of a significant network disruption that hindered global internet traffic for multiple hours, impacting millions of users and various platforms. The disruption, which commenced at 11:20 UTC,...

Cyber Security
“`html IBM has issued significant security patches that address two critical vulnerabilities in its AIX operating system, which could permit remote intruders to execute arbitrary commands on vulnerable systems. Both weaknesses arise from inadequate process...
Cyber Security
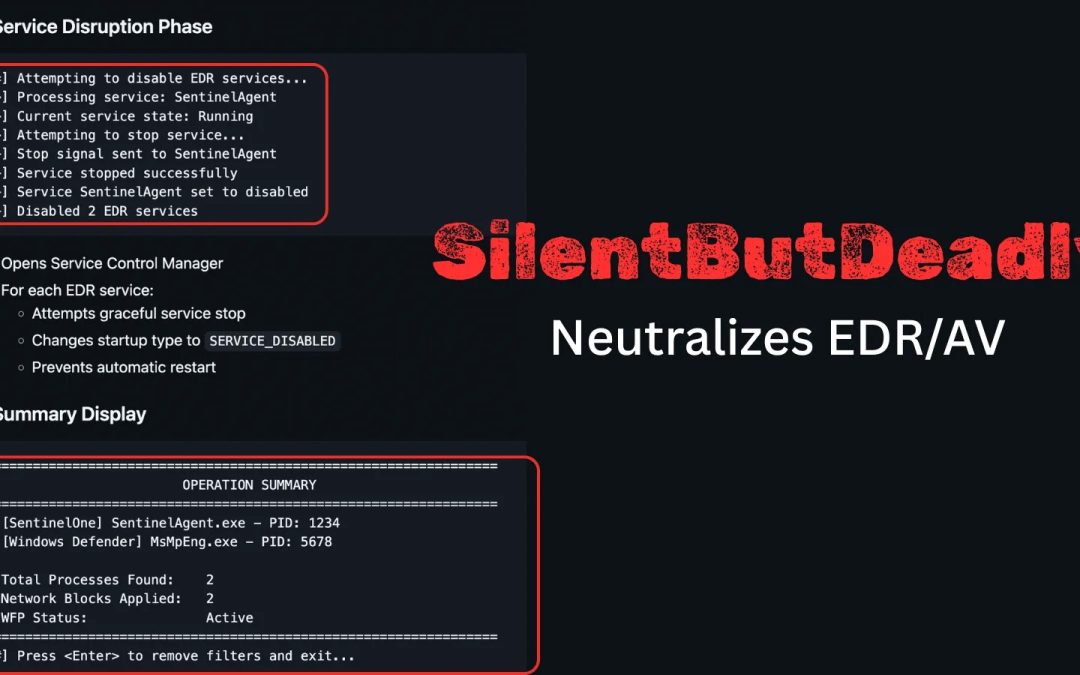
“`html A recent open-source application named SilentButDeadly has surfaced, designed to interfere with Endpoint Detection and Response (EDR) and antivirus (AV) programs by disrupting their network interactions. Created by security analyst Ryan Framiñán, the...

Cyber Security
“`html A critical security vulnerability in Cisco Catalyst Center Virtual Appliance has been uncovered, permitting attackers with minimal access to achieve full administrative control over the vulnerable systems. The flaw, designated as CVE-2025-20341, affects...

Cyber Security
“`html Fortinet has released an urgent notification cautioning about a serious flaw in its FortiWeb web application firewall (WAF) solution, which cybercriminals are currently exploiting in the field. Named CVE-2025-64446, the vulnerability arises from...

Cyber Security
“`html Threat actors are currently exploiting a significant authentication bypass weakness in Fortinet’s FortiWeb web application firewall (WAF) across the globe, urging defenders to enhance their alertness. Investigators at watchTowr Labs have countered by...

Cyber Security
“`html A security flaw has been identified in Lite XL, a minimalistic text editor, which may permit attackers to run arbitrary code on compromised systems. Experts from Carnegie Mellon University discovered CVE-2025-12120, which impacts Lite XL versions 2.1.8...

Cyber Security
“`html Danabot, a well-known banking Trojan, has re-emerged significantly with its latest version 669 following a hiatus prompted by Operation Endgame’s law enforcement operation in May 2025. This advanced malware’s resurgence indicates a fresh wave of threats...

Cyber Security
“`html Cybercriminals are progressively targeting websites to insert harmful links while enhancing their search engine optimization standings through elaborate blackhat SEO strategies. This initiative mainly centers around online casino spam, which has emerged...











