Storm-1811, a financially motivated threat actor utilizing social manipulation tactics, has recently been identified leveraging RMM utilities to disseminate the Black Basta ransomware.
This threat actor takes advantage of the customer administration tool, Microsoft Quick Assist, with the aim of deploying Black Basta ransomware as the primary malicious payload across the network.
Quick Assist is a software application that allows a user to remotely link to another individual and share their Windows or macOS system.
This enables the connecting user to observe the display of the device, make notes, or assume complete control—often for the purpose of resolving issues—by remotely linking to the recipient user’s system.
Exploring the Tactics of Storm-1811
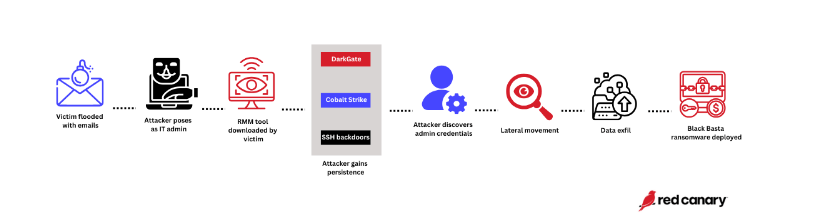
According to Red Canary, the recently detected operation began with inundating a victim’s inbox with spam emails, a technique known as email flooding.
Subsequently, the aggressor, masquerading as an IT administrator, offers assistance with the email problem by either calling the user or sending them a link to join a Microsoft Teams meeting.
After establishing contact, the attacker directed the user to download and initiate AnyDesk or TeamViewer or launch Microsoft Quick Assist for granting remote access. The attack encompassed lateral traversal, reconnaissance, and the establishment of an SSH tunnel backdoor.
Black Basta was initially unearthed in April 2022 and is recognized as a ransomware-as-a-service (RaaS) variant. Black Basta affiliates have impacted crucial infrastructures and diverse industries in Australia, Europe, and North America.
As per CISA’s most recent alert, over 500 organizations globally have been affected by Black Basta affiliates by May 2024.
Affiliates of Black Basta employ a dual-extortion approach, encrypting systems and extracting data after exploiting common initial entry methods like phishing and capitalizing on known vulnerabilities.
Countermeasures
- Implement detection and response sensors across all systems.
- Undetected endpoints serve as a playground for attackers; monitoring limits the movement of the opponent.
- Maintain a register of authorized tools and obstruct or limit unauthorized RMM utilities.
- Legitimate utilities can be manipulated, so understanding your environment is crucial.
- To enhance the security of Microsoft Teams, block external access by default, allow only reputable partner domains, and regulate file-sharing privileges to prevent unauthorized software.
The article “Storm-1811 Hackers Exploits RMM Tools to Deliver Black Basta Ransomware” was first published on Cyber Security News.