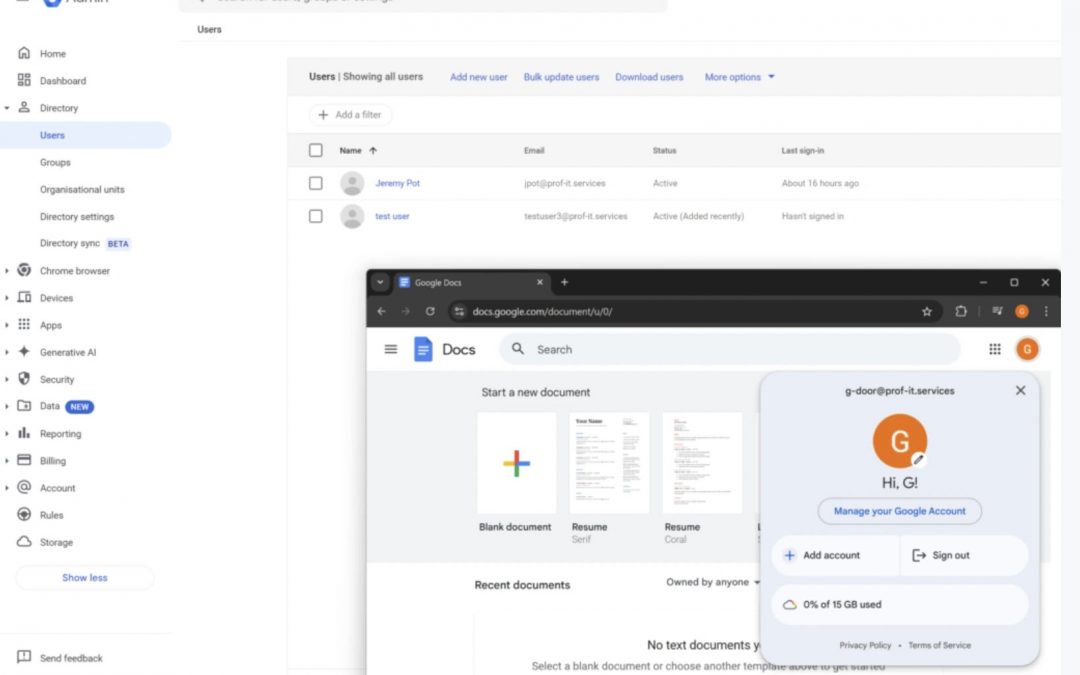
A recently discovered weakness, named “G-Door,” enables nefarious individuals to evade Microsoft 365 security protocols by leveraging unmanaged Google Docs accounts. This security vulnerability presents a significant risk to enterprises depending on Microsoft 365’s Conditional Access (CA) guidelines for safeguarding.
The G-Door flaw arises from the capacity to establish personal or work Google accounts using a corporate domain. Through these uncontrolled accounts, users can access third-party applications, eluding Microsoft 365’s security mechanisms.
Risks Associated with the G-Door Vulnerability
- Bypassing Conditional Access: Users or attackers can form Google accounts using corporate email addresses, bypassing critical security checkpoints like multi-factor authentication (MFA), device compliance assessments, and geolocation constraints.
- Lack of Transparency: Actions from these unmanaged accounts do not register in Microsoft 365 Admin Center logs, impeding incident response and anomaly detection.
- Data Exposure: Confidential data stored in Google Drive or produced in Google Docs is not protected by corporate Data Loss Prevention (DLP) or Azure Information Protection (AIP) policies.
- Continuous Access: Intruders who compromise a Microsoft 365 account can establish a distinct Google identity, retaining access to third-party applications even post the initial credentials revocation.
- Substandard Account Offboarding: Former employees may continue unauthorized access to linked applications or data vaults via unmanaged Google accounts after departing the company.
Users have the option to swiftly create personal Google accounts or enroll in the complimentary Google Docs Essentials Starter scheme using their corporate email addresses.
This procedure necessitates no administrative consent and can be finalized within minutes, assigning users an unmanaged Google identity affiliated with the company’s domain.
The G-Door vulnerability compromises numerous core security elements of Microsoft 365:
- Conditional Access rules lose effectiveness for these unmanaged accounts.
- Device compliance and geolocation restrictions can be overridden.
- Data protection mechanisms and legal compliance endeavors are jeopardized.
- Group-oriented access controls in Azure AD (Entra) can be skirted.
To counteract the G-Door vulnerability, organizations are advised to:
- Enforce stringent domain validation procedures for Google Workspace.
- Regularly scrutinize and administer unmanaged accounts linked to the corporate domain.
- Augment user awareness regarding the hazards of creating personal accounts utilizing work email addresses.
- Contemplate deploying supplementary third-party security solutions to oversee and regulate access across diverse cloud platforms.
Given the escalating reliance on cloud-based productivity suites by organizations, addressing exposures like G-Door is paramount for upholding a resilient security stance. IT administrators and security experts need to stay alert and adapt their approaches to counteract these emerging perils.
The article “New G-Door Vulnerability Lets Hackers Bypass Microsoft 365 Security With Google Docs” was first published on Cyber Security News.