Performing malware examination may appear as a lengthy and intricate assignment, however, with the correct tools and methodologies, it can be accomplished in just a matter of minutes.
By following 5 straightforward steps, you can uncover even the most cunning malware activities, making it simple to evaluate and address threats with assurance.
Collecting Samples and Initial Inspection
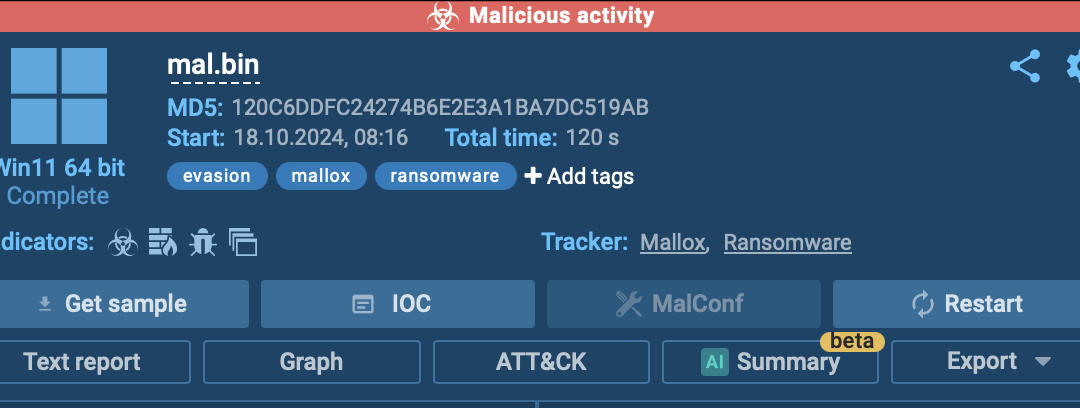
Commence by utilizing a malware testing environment, such as ANY.RUN, to scrutinize your specimen in a secluded and secure location. Insert a URL or upload a file through ANY.RUN’s interface, where you can also set up the analysis setup.
Once the testing environment is initiated, the top right segment will signal if the specimen is malevolent. If so, it will be highlighted in red and labeled as “malicious behavior.” This portion further exhibits tags of the dangers connected with the specimen, offering a swift evaluation of the risk level.
For instance, in the ongoing examination session, the testing environment detected malicious behavior, encompassing a malware entity named Mallox. Examine the session analysis.
Engage with the Sample
While the examination session is active, you can monitor the conduct of the potential threat in real-time. Freely interact with the specimen, mimicking user actions like selecting buttons, browsing websites, and uploading files, all within a secured environment.
This hands-on interaction assists in comprehending how the malware operates in a practical environment, revealing activities it might engage in when deployed on an authentic device.
In the ongoing investigation session, we observe all the activities executed by the malware, including the ransom letter the target receives following the attack.
Inspect Processes
To delve into the specifics, testing environments like ANY.RUN enable you to assess all processes instigated during the examination.
You may view elaborations by selecting each process, from network connections and HTTP requests to DNS queries and other system undertakings. For more detailed insights on any particular process, click the “Further Details” option.
Acquire a Textual Report
ANY.RUN eases the process of generating reports with its “Text Report” feature, situated on the right-hand side of the screen. With a single tap, you gain access to a detailed report outlining all processes, network activities, and other indications of compromise (IOCs) detected during the examination.
This report is pivotal for cataloging and distributing discoveries, as it captures the entire behavioral profile of the malware.
Compile IOCs
Indicators of Compromise (IOCs) are paramount for identifying and curtailing the dissemination of malware across your network. Within the testing environment, you can accumulate all IOCs from the examination by selecting the “IOC” button, which consolidates everything from IP addresses to suspicious domains in a well-organized panel.
These IOCs fortify your defenses and empower security teams to recognize and obstruct related threats effectively.
Evaluate Malware in Minutes
Through ANY.RUN’s interactive testing environment, malware analysis can be simplified and expedited. It offers unrestricted privileges for securely scrutinizing malware specimens within an insulated setting.
Enroll in ANY.RUN today for prompt, effortless, and unlimited access to comprehensive malware analysis!
The article Malware Analysis in 5 Simple Steps was first published on Cyber Security News.