Malevolent hackers employ an advanced evasion scheme known as ZIP bundle merging to target Windows users in particular. This maneuver involves amalgamating multiple ZIP files into a singular archive, complicating the detection of harmful content by security software.
This method may lead unsuspecting users to unknowingly download detrimental files, mistakenly believing they are accessing secure, compressed data.
Such a strategy enables attackers to circumvent conventional security measures and distribute malware without detection, presenting substantial hazards to individuals and organizations alike.
Through exploiting the varied processing of concatenated files by different ZIP readers, threat actors can insert malicious payloads into archives that escape scrutiny by many standard security tools.
Technique of ZIP File Concatenation
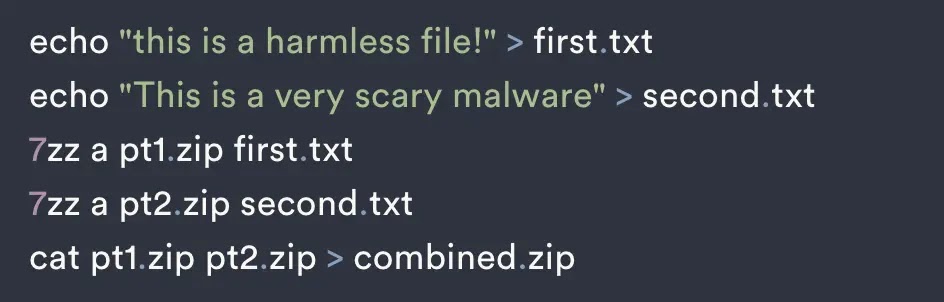
The process of ZIP bundle merging entails appending multiple ZIP archives into a single file. Despite appearing as a unified archive, this combined file actually consists of multiple central directories, each indicating different sets of files.
Per Perception Point, the effectiveness of this technique hinges on how different ZIP readers interpret the concatenated structure. Certain readers may only exhibit the contents of one archive while disregarding the others, thereby allowing hidden malicious files to evade detection.
For example, if two ZIP files are concatenated—one containing benign content and the other housing malware—specific tools will only showcase the harmless files. This inconsistency in handling allows assailants to cloak their payloads from detection tools reliant on particular ZIP readers.
Prominent ZIP readers like 7zip, WinRAR, and Windows File Explorer handle concatenated ZIP files in distinctive ways:
- 7zip: When initiating a concatenated ZIP file using 7zip, solely the contents of the initial archive are visible. While 7zip might give a heads-up about excess data post the end of the archive, users often overlook this.
- WinRAR: Differing from 7zip, WinRAR interprets the second central directory and reveals all contents, including any concealed malicious files. This enhances its effectiveness in detecting threats concealed within merged archives.
- Windows File Explorer: The native archive handler of Windows struggles with concatenated ZIPs, occasionally failing to open the file or only displaying a fragment of its contents. This inconsistency diminishes its reliability in uncovering camouflaged threats.
A recent assault sheds light on how threat actors utilize this technique to propagate malware. In this instance, unsuspecting victims received a phishing email camouflaged as a shipping notification detailed in the report.

The email attachment was named “SHIPPING_INV_PL_BL_pdf.rar,” masquerading as a RAR file but actually being a concatenated ZIP archive.
Upon opening with 7zip, the file only displayed an innocuous-looking PDF document. However, upon using WinRAR or Windows File Explorer, the concealed malicious executable “SHIPPING_INV_PL_BL_pdf.exe” was unveiled.
This executable was identified as a variant of Trojan malware devised to automate malicious functions like downloading additional payloads or executing ransomware.
The success of this evasion tactic stems from its exploitation of the differences in how various utilities process ZIP files. Numerous security solutions depend on common ZIP handlers like 7zip or native OS utilities to scan archives for malicious content.
Given that these utilities may not comprehensively dissect concatenated archives, they can entirely overlook hidden threats.
Hackers are increasingly resorting to this strategy as it enables them to pinpoint certain users who rely on specific tools while evading detection by others. For example, Windows users dependent on built-in utilities or 7zip may face a higher susceptibility to succumbing to such assaults
The article Hackers Use ZIP File Concatenation Tactic to Launch Undetected Attacks on Windows Users appeared first on Cyber Security News.