Silver and Cobalt Strike are advanced adversary simulation tools that see widespread usage in penetration testing and red team operations.
These tools give security analysts the ability to imitate sophisticated persistent threats through features such as “covert command and control channels” and “post-exploitation capabilities.”
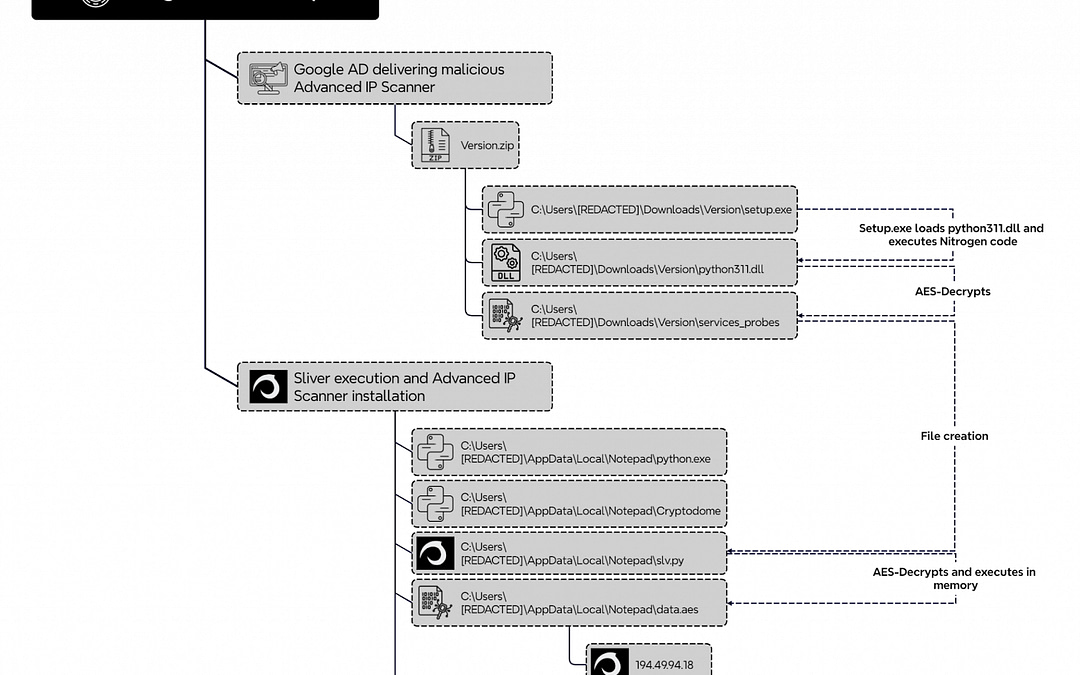
Recently, security experts at “The DFIR Report” uncovered Nitrogen malware, disguised as “IP Scanner,” which was observed deploying Sliver and Cobalt Strike on a compromised server.
Implementing Silver & Cobalt Strike
An unwitting user downloaded malware posing as “Advanced IP Scanner” from a deceitful website advertised via “Google ads,” initiating a deceptive “Nitrogen campaign.”
The malicious payload was distributed as a “ZIP file,” containing a “valid Python executable” (“setup.exe”) that loaded a “modified python311.dll,” triggering the Nitrogen code.
This led to the activation of “Sliver” and “Cobalt Strike” beacons, refined “remote access tools,” made intricate using “Py-Fuscate.”
By utilizing “PowerView” and “BloodHound” to chart the network and Active Directory design, the attacker carried out extensive reconnaissance spanning eight days.
Moreover, they engaged in lateral movement through “Windows Management Instrumentation (WMI),” “Remote Desktop Protocol (RDP),” and “Pass-the-Hash techniques.”
Through the extraction of credentials by dumping LSASS memory, the attacker sustained persistence via “scheduled tasks,” “registry alterations (WinlogonUserinit key),” and fabrication of processes resembling legitimate entities such as ‘OneDrive’ and ‘Microsoft Edge.’
They employed diverse defense evasion strategies like “API unhooking,” “sleep obfuscation,” and circumventing ‘AMSI,’ ‘WLDP,’ and ‘ETW.’
To escalate privileges through process injection into “winlogon.exe,” data exfiltration was accomplished using the open-source backup software “Restic,” sending files to a server in “Bulgaria.”
In the final stage, the attacker initiated “BlackCat” ransomware across the network using the “Server Message Block (SMB)” protocol and “PsExec.”
They coerced systems to boot into “Safe Mode” with Networking to bypass security measures, leveraging the ‘compromised backup service account’ for automatic login via “Winlogon.”
This facilitated the wide dissemination of file encryption and left ransom notes on the “impacted hosts.” The Time to Ransomware (TTR) reached around 156 hours, spanning eight calendar days from the initial breach to complete deployment, as per the DFIR report.
The incident involved threat actors utilizing C2 servers established in “Bulgaria” and “the Netherlands.”
On ‘port 441,’ threat actors leveraged “Cobalt Strike” with specific IP addresses (“91.92.250.158,” “91.92.251.240,” “94.156.67.175,” “94.156.67.180”) and an “untrusted HTTPS certificate” (serial number “1657766544761773100”).
Employing invalid certificates, the attackers also implemented “RedGuard” and “Sliver” on servers. To transfer sensitive data over ‘HTTP’ to a server at “195.123.226.84:8000,” they utilized “Restic”
To deploy batch scripts (‘up.bat’ and ‘1.bat’) across the network, threat actors executed remote commands using “PsExec.”
These scripts executed the following crucial actions:-
- Resetting passwords.
- Modifying system boot configurations.
- Establishing auto-login mechanisms.
Additionally, the final phase entailed deploying ransomware, which ‘ciphered files,’ ‘erased volume shadow copies’ to impede easy recovery, and left a ‘ransom note.’
Throughout the assault, threat actors employed various Windows utilities like “bcdedit,” “reg,” and “shutdown” to alter system configurations and ensure continuity.
The post Nitrogen Malware As IP Scanner Deploying Sliver & Cobalt Strike On Hijacked Server appeared first on Cyber Security News.