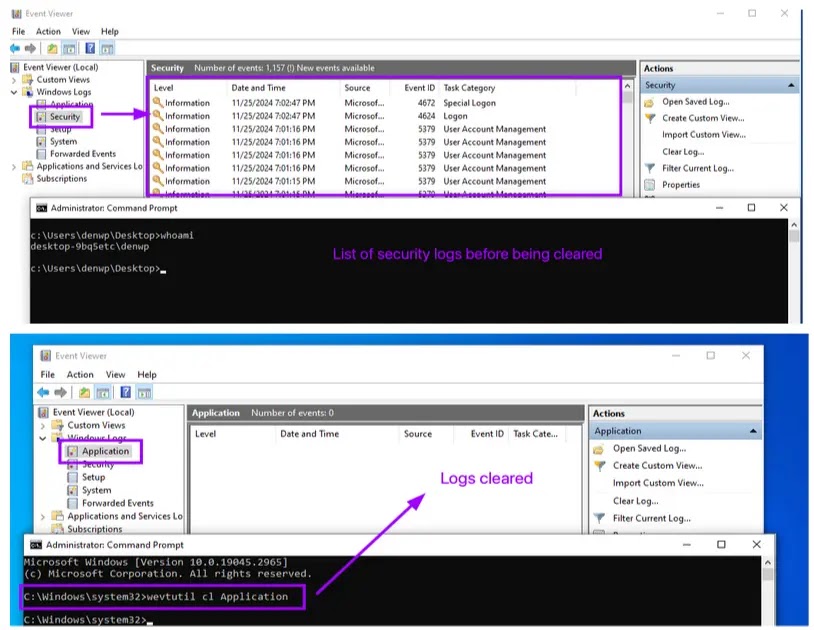
Wevtutil.exe, a utility in the Windows event log system, can be misused in Living Off the Land (LOLBAS) techniques to export logs for exfiltration, retrieve specific event data, or clear logs.
The utilization of Living Off the Land Binaries and Scripts (LOLBAS) tactics by attackers is on the rise.
These methods capitalize on reliable, pre-installed Windows utilities to execute malicious operations, often bypassing security measures undetected.
The Denwp Research blog notes, “In a LOLBAS context, Wevtutil.exe can be manipulated to clear, query, or export event logs, aiding attackers in remaining undetected and stealing data.”
Being inherently present on Windows systems, Wevtutil.exe serves as an effective and inconspicuous tool for post-exploitation endeavors.
Exploiting The Windows Event Log Utility
System administrators often rely on Wevtutil.exe to gather and manage logs for auditing or troubleshooting purposes. Nonetheless, the capabilities of Wevtutil.exe can be harnessed for malevolent deeds.
Notable functionalities of Wevtutil.exe include:
- Exporting event logs to XML format.
- Clearing specific or all event logs.
- Querying event logs based on defined criteria.
Wevtutil.exe presents a dilemma due to these capabilities; while beneficial for legitimate tasks, it can also aid attackers in covering their tracks or pilfering data.
Attackers can utilize ‘Wevtutil cl’ to delete individual logs either selectively or entirely.
Although not a new methodology, employing unconventional tools can help skirt detection systems that primarily target mainstream applications like PowerShell.
Researchers affirm that application logs can be effectively cleared via an elevated command prompt.
Within the Windows Event Viewer, Event ID 1102 is generated upon the clearance of the Security log. This event signifies the erasure of audit logs, a critical security indicator.
For defenders and security monitoring solutions, Event ID 1102 stands out due to the inclusion of details like the login credentials and process responsible for the log-clearing action.

By default, Windows does not log events indicating the deletion of non-security logs like Application or System. Administrators can counter this by activating Audit Policies to watch over log removal operations.
Furthermore, the ‘wevtutil qe’ command empowers Wevtutil.exe to export event logs in XML format. These logs may harbor sensitive data that attackers could mine and exfiltrate, including credentials or indicators of internal activities.
Wevtutil.exe facilitates precise log querying, granting attackers insights into user or system activity.
Adversaries can retrieve details on privileged tasks, system malfunctions, or authentication endeavors by crafting customized queries.
Incorporating Wevtutil.exe into a chain of LOLBAS tools can further obfuscate activities. For instance, a threat actor could:
- Export logs using Wevtutil.exe.
- Compress the exported file with makecab.exe.
- Utilize certutil.exe to transmit the file to a remote destination.
Organizations ought to bolster monitoring capabilities, ensure event log integrity, and employ behavioral analytics to counter the escalating misuse of Wevtutil.exe.
Enabling advanced audit policies can heighten detection capabilities and log events even for non-Security log categories.
Furthermore, comprehending these behaviors is pivotal for red teams leveraging this utility and defenders striving to pinpoint and mitigate its misuse.
The post Hackers Exploited Windows Event Logging Tool To Steal Data Secretly appeared first on Cyber Security News.