ESET analysts have discovered two crucial previously unknown weaknesses in WPS Office for Windows, which have been utilized by the APT-C-60 advanced persistent threat group.
This cyberespionage group aligned with South Korea has been focusing on users in East Asian regions, exploiting these flaws to run malicious code and deploy malware.
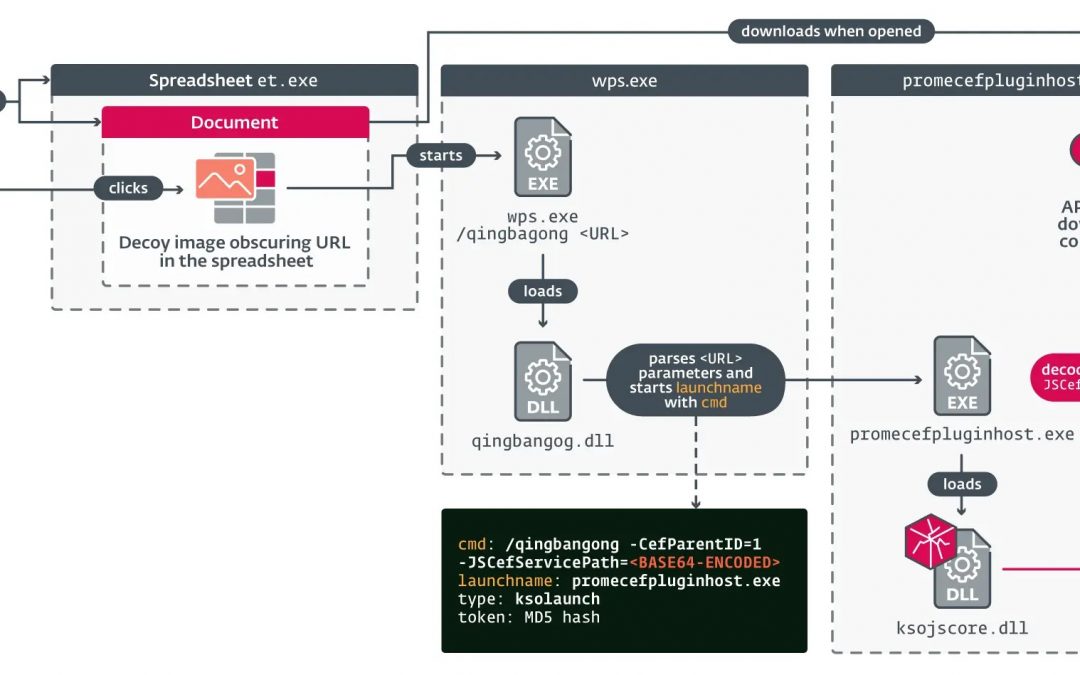
The first vulnerability, acknowledged as CVE-2024-7262, concerns a flaw in the WPS Office plugin element, known as promecefpluginhost.exe.
The weakness emerges due to inadequate sanitization of file paths provided by attackers and insufficient verification of loaded plugins.
This loophole empowers attackers to take over the application’s control flow, enabling the execution of any specified code. The exploitation procedure includes creating a corrupted spreadsheet document that, upon opening in WPS Office, triggers the activation of a custom backdoor named SpyGlace. This backdoor, also recognized as TaskControler.dll, is utilized to distribute malware onto the targeted systems.
The attack approach of APT-C-60 includes employing an MHTML file format, which is a multifaceted archive capable of accommodating HTML, CSS, and JavaScript files.
By using this format, the attackers can implant a concealed hyperlink within the document. User interaction with this hyperlink leads to remote execution of malicious code by downloading a library from an external file path.
The attackers take advantage of the ksoqing protocol handler registered by WPS Office to execute external applications through carefully crafted URLs.
The second vulnerability, CVE-2024-7263, was uncovered during the assessment of the patch for CVE-2024-7262. This vulnerability also involves code execution via the same plugin component but leverages a distinct logic flaw.
The issue lies in how command line arguments are managed improperly, allowing attackers to evade checks and load malicious libraries without adequate signature validation. This vulnerability accentuates the necessity of comprehensive patching to tackle all possible exploitation avenues.
WPS Office enjoys widespread usage, catering to over 500 million active users globally, which makes it an appealing target for cybercriminals. These vulnerabilities have been actively exploited, primarily impacting users in East Asia.
By capitalizing on these vulnerabilities, APT-C-60 demonstrates their sophistication and persistence in targeting users in their region.
After the discovery, ESET cooperated with Kingsoft, the developers of WPS Office, to rectify these vulnerabilities. Despite initially patching CVE-2024-7262 discreetly, further investigation revealed that the patch was incomplete, leaving certain sections of the code exposed.
Kingsoft has since acknowledged and fixed both vulnerabilities, advising users to update their software to the latest version to mitigate the associated risks from these exploits.
The exploitation of zero-day vulnerabilities in WPS Office by APT-C-60 serves as a stark reminder of the persistent threats posed by sophisticated cyber espionage groups.
It is highly recommended for organizations and individuals utilizing WPS Office to promptly update their software and remain alert against potential phishing endeavors and suspicious documents.
The impacted versions of WPS Office for Windows span from 12.2.0.13110, released approximately in August 2023, until the rollout of the patch towards the end of May 2024 with version 12.2.0.17119.
The article APT Hackers Exploiting Zero-Day Vulnerabilities in WPS Office was first published on Cyber Security News.