Endpoint security has emerged as a critical concern for organizations of all magnitudes. Considering the escalating and widespread cyber threats, the significance of an Endpoint Protection Platform (EPP) has never been more crucial.
This article delves into the comprehensive understanding of an EPP, the distinction between Endpoint Detection and Response (EDR), and the necessity of it for contemporary enterprises.
We shall also delve into selecting the appropriate EPP, the advantages it provides, and a comparative analysis of EPP and EDR features presented in a tabular form.
Grasping the Endpoint Protection Platform
An Endpoint Protection Platform (EPP) refers to an integrated collection of endpoint security technologies, devised to safeguard endpoint devices from security breaches.
These platforms amalgamate diverse tools such as antivirus, data encryption, and data loss prevention to detect and nullify threats like file-based malware and malevolent activities.
Cutting-edge EPPs employ multiple recognition techniques, often supervised and aided by cloud data, to provide robust protection.
EPPs operate by gathering extensive endpoint data and employing tools such as artificial intelligence (AI), behavioral analysis, and threat intelligence to anticipate and counter potential threats. This proactive approach is pivotal in thwarting breaches and securing sensitive information.
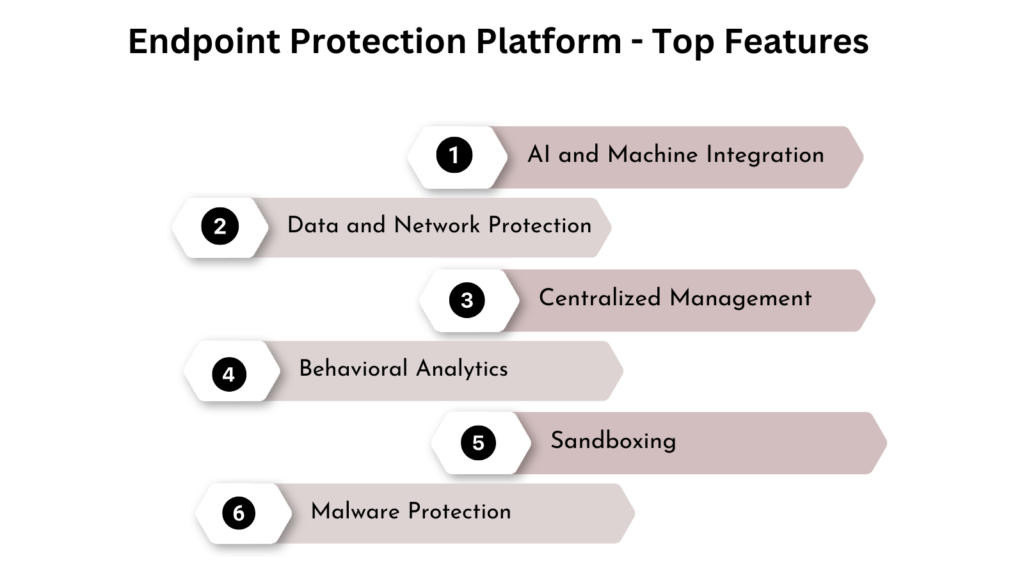
Principal Features of an EPP
- Antivirus and Antimalware: Crucial utilities for recognizing and eliminating known threats.
- Data Encryption: Shields sensitive data stocked on endpoints.
- Firewall: Presents a barricade against unauthorized entry.
- Behavioral and Static Analysis: Supervises endpoint behavior for anomalies.
- Threat Intelligence Integration: Utilizes global threat data to enrich security measures.
EPP vs. EDR: Comprehending the Disparities
While both EPP and EDR are vital constituents of endpoint security, they serve disparate objectives and harbor distinctive traits. Here’s an exhaustive evaluation:
| Feature | Endpoint Protection Platform (EPP) | Endpoint Detection and Response (EDR) |
| Primary Focus | Preventive security strategies | Proactive cybersecurity fortification and response |
| Main Function | Averts known cyber assaults and diminishes endpoint security breaches | Identifies, scrutinizes, and responds to potential threats that circumvent initial defenses |
| Key Capabilities | Antivirus, Firewall, Data Encryption, Allow listing and blocklisting | Ongoing security monitoring, Real-time visibility, Threat analysis, Automated response |
| Behavioral and static analysis | Forensics analysis | |
| Monitoring Approach | Monitors for known suspicious code signatures | Offers continuous monitoring of local and remote devices |
| Response Mechanism | Highlights suspicious conduct for scrutiny and action | Administers automated responses grounded on predetermined regulations |
| Ideal Management Team | General IT teams | Security operations center teams |
| Threat Handling | Primarily manages known threats | Competent in detecting and responding to unknown and sophisticated assaults |
| Additional Features | Threat hunting, threat intelligence, vulnerability management (in some EPPs) | Sandbox isolation for suspicious code, insider threat monitoring |
Opting for the Appropriate Endpoint Protection Platform
Choosing the right EPP encompasses several pivotal steps to ensure it aligns with organizational requisites and offers efficacious protection.
1. Specify Requirements
Initiate by outlining the precise security obligations and priorities of your organization. Take into account aspects like the kinds of data managed, regulatory mandates, and the variety of endpoints.
2. Investigate and Shortlist
Utilize analyst insights, peer assessments, and industry standards to compile a shortlist of potential EPP vendors. Evaluate each choice based on prestige, dependability, and feature array.
3. Evaluate System Footprint
Assess the impact of the EPP on system performance, encompassing CPU utilization and memory consumption. An efficient EPP should shield without significantly obstructing device performance.
4. Confirm Integration Compatibility
Ascertain that the EPP can seamlessly intertwine with existing security utilities and IT infrastructure. Compatibility with diverse operating systems and device categories, inclusive of portable devices, is imperative.
5. Appraise Management Attributes
Search for a user-friendly management dashboard that simplifies policy configuration, threat examination, and overall platform management.
6. Execute Assessments
Conduct trial runs to evaluate real-world performance and adequacy. This stage is vital for comprehending how the EPP will function under authentic circumstances.
7. Analyze Agreement Terminology
Meticulously scrutinize service-level agreements and support conditions to ensure they meet organizational necessities and anticipations.
Merits of an Endpoint Protection Platform
Deploying a dependable EPP bestows myriad benefits, including:
- Unified Management: Supervise all portable and stationary endpoint devices through a singular system.
- Enhanced Security: Safeguard against threats while preserving endpoints adaptable for users.
- Security Gap Identification: Detect and eliminate security breaches, fortifying comprehensive protection.
- Simplified Management: Rationalize processes for analysts and IT staff, enhancing efficiency.
- Reputation Protection: Secure endpoints to preserve and augment business reputation.
- Business Resilience: Bolster organizational resilience against cyber threats.
Rationale Behind Endpoint Protection
Endpoint protection constitutes a pivotal constituent of any organization’s security blueprint for myriad reasons:
- Escalating Endpoint Diversity: The accelerated proliferation in the count and assortment of endpoints, encompassing portable devices and IoT, poses new challenges for security teams. This variety amplifies the attack surface, rendering thorough protection imperative.
- Endpoints as Principal Attack Portals: Cyber malefactors frequently zero in on endpoints to pilfer data, infiltrate networks, or unleash ransomware. Shielding these vulnerable points is crucial to fortify digital assets, encompassing identities and credentials.
- Trends in Remote and Hybrid Work: With a multitude of employees operating remotely, oftentimes from insecure environments, robust endpoint protection is indispensable. Remote devices may not invariably utilize the latest security solutions, necessitating robust endpoint defenses.
Upcoming Trends in Endpoint Protection
As technology progresses, endpoint protection platforms are anticipated to evolve into more intricate entities. Key trends comprise:
- AI and Machine Learning: These technologies will assume a grander role in threat detection and response, facilitating swift and precise threat identification.
- Integration with Zero Trust Architecture: EPPs will increasingly fuse with zero trust frameworks, ensuring that no device is inherently trusted, and all access is continually verified.
- Cloud-Based Solutions: With the burgeoning cloud adoption, EPPs will capitalize on cloud platforms for enhanced data scrutiny and real-time threat intelligence.
- Emphasis on User Behavior: Comprehending user behavioral patterns will metamorphose into a pivotal facet in recognizing anomalous activities and plausible insider threats.
An Endpoint Protection Platform is an indispensable instrument in the cybersecurity arsenal of any contemporary organization.
By comprehending its attributes, merits, and the distinctions between EPP and EDR, enterprises can make well-informed decisions to efficiently safeguard their digital assets.
The post What is an Endpoint Protection Platform? Key Features and Benefits appeared first on Cyber Security News.